Cisco 4402 Configuration Guide - Page 51
Step 4: Connection Request Policies
 |
UPC - 882658039997
View all Cisco 4402 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 51 highlights
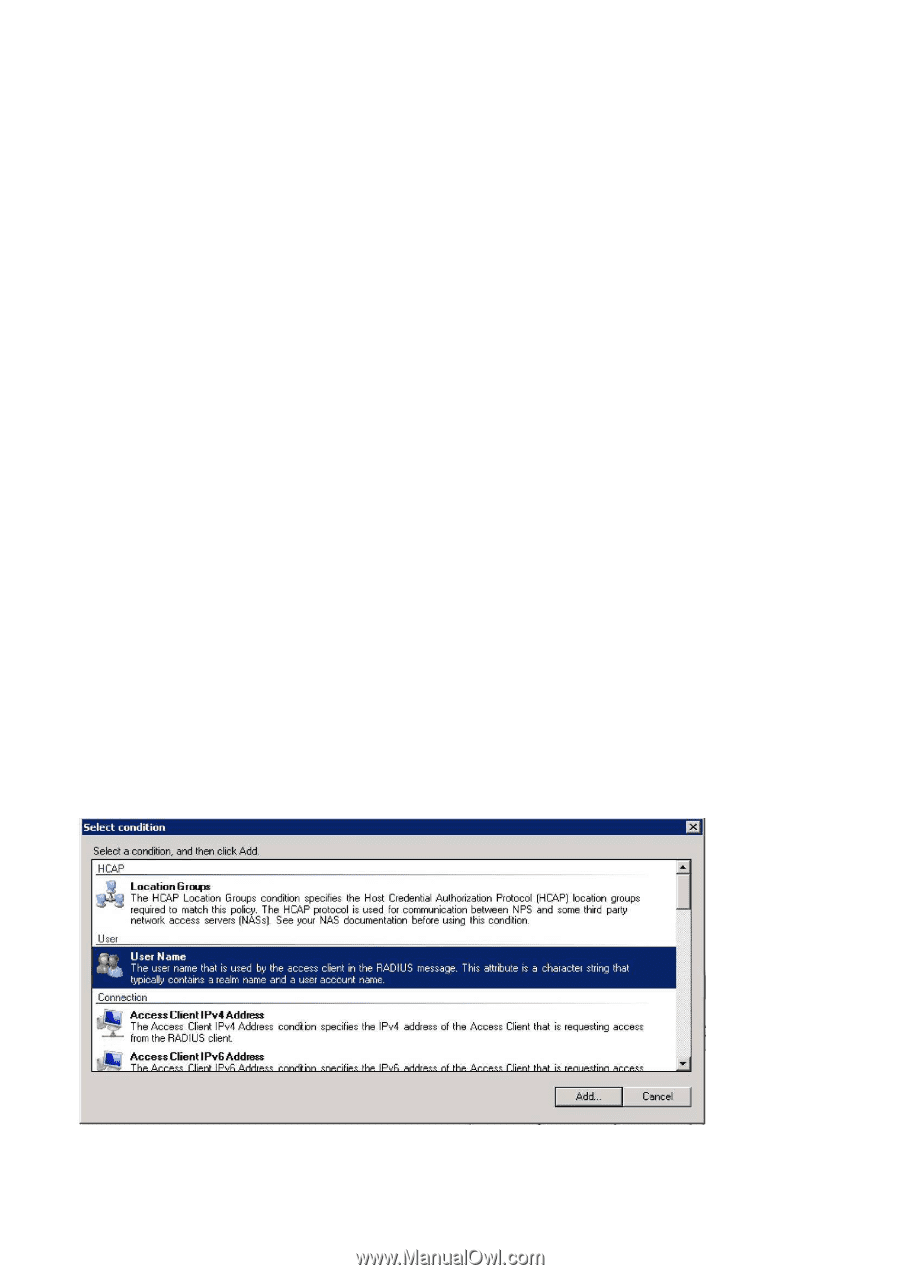
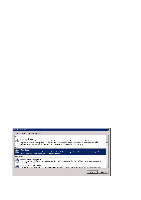
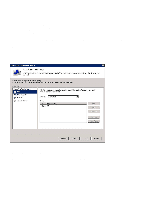
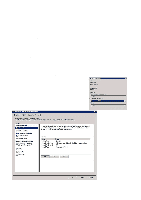
Step 4: Connection Request Policies Connection Request Policies determine where authorisation shall take place according to certain criteria. One policy may authenticate employees locally and forward all students to the RADIUS server associated with the school domain, while another policy directs all other users to the eduroam core. Since the policies are handled in a specified order, it is important that this is done correctly. 1. Users who are to be authenticated locally 2. Users who are to be forwarded to another RADIUS server (several of which can be configured) 3. All other users to be directed to eduroam • Expand "Policies", right-click on "Connection Request Policy" and select "New" • Type in the Policy name (for example, "Local", "School" or "eduroam") and click on "Next" • Click on "Add" to add criteria for the connection. eduroam determines where a user belongs by using the realm which is indicated when the user types username@organisation. In spite of the apparent similarity, there is no connection between realm and e-mail address. However, in most cases it is possible to use a realm corresponding to an e-mail address. The realms used are often agreed in advance. If you have any queries, contact [email protected] An example of a realm: student.school.no is the connection to eduroam and forwards authentication to the employee.school.no RADIUS server. The "Employee" RADIUS server is the last in the series and receives authentication requests it shall use and forwards them. Criteria for Connection Policies on the student.school.no RADIUS server: .*@student.school.no - All students, authenticated locally .*@employee.school.no - All employees, sent to the "Employee" RADIUS server .*@.* - All other users, sent to the "Employee" RADIUS server Criteria for Connection Policies on the "Employee" RADIUS server: .*@employee.school.no - All employees, authenticated locally .*@.* - All other users, sent to the eduroam server • Select "User-Name" and click on "Add". Fill in the criteria, for example ".*@student.school.no" specifies that all users who type in [email protected] shall be authenticated using this policy. • Click on "OK" followed by "Next" The "Authentication" option controls where the authentication is to be directed to. 51