Cisco 6941 Administration Guide - Page 84
Settings > Security Configuration > 802.1X, Security Config > 802.1X Authentication > - cp -
 |
UPC - 882658277801
View all Cisco 6941 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 84 highlights
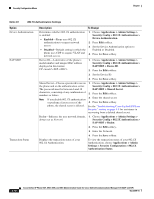
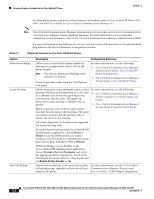
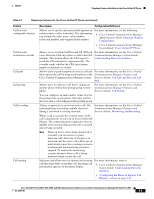
Security Configuration Menu Chapter Table 4-5 802.1X Authentication Settings Option Device Authentication EAP-MD5 Transaction Status Description To Change Determines whether 802.1X authentication is enabled: • Enabled-Phone uses 802.1X authentication to request network access. • Disabled-Default setting in which the phone uses CDP to acquire VLAN and network access. 1. Choose Applications > Admin Settings > Security Config > 802.1X Authentication > Device Authentication. 2. Press Edit softkey. 3. Set the Device Authentication option to Enabled or Disabled. 4. Press the Save softkey. Device ID-A derivative of the phone's model number and unique MAC address displayed in this format: CP--SEP- 1. Choose Applications > Admin Settings > Security Config > 802.1X Authentication > EAP/MD5 > Device ID. 2. Press the Edit softkey. 3. Set the Device ID. 4. Press the Save softkey. Shared Secret-Choose a password to use on the phone and on the authentication server. The password must be between 6 and 32 characters, consisting of any combination of numbers or letters. Note If you disable 802.1X authentication or perform a factory reset of the phone, the shared secret is deleted. 1. Choose Applications > Admin Settings > Security Config > 802.1X Authentication > EAP-MD5 > Shared Secret. 2. Press the Edit softkey. 3. Enter the shared secret. 4. Press the Save softkey. See the "Troubleshooting Cisco Unified IP Phone Security" section on page 9-8 for assistance in recovering from a deleted shared secret. Realm-Indicates the user network domain, 1. Choose Applications > Admin Settings > always set as Network. Security Config > 802.1X Authentication > EAP-MD5 > Realm. 2. Press the Edit softkey. 3. Enter the Network. 4. Press the Save softkey. Displays the transaction status of your 802.1X Authentication. To view the transaction status of your 802.1X Authentication, choose Applications > Admin Settings > Security Configuration > 802.1X Authentication Status. 4-10 Cisco Unified IP Phone 6921, 6941, 6945, and 6961 Administration Guide for Cisco Unified Communications Manager 8.5 (SCCP and SIP) OL-23769-01