D-Link DES-3828 Product Manual - Page 150
CPU Interface Filtering, Packet Content
 |
UPC - 790069276811
View all D-Link DES-3828 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 150 highlights
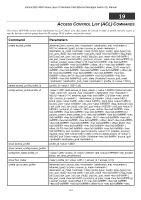
xStack DES-3800 Series Layer 3 Stackable Fast Ethernet Managed Switch CLI Manual Now that an access profile has been created, you must add the criteria the Switch will use to decide if a given frame should be forwarded or filtered. Here, we want to filter any packets that have an IP source address between 10.42.73.0 and 10.42.73.255: config access_profile profile_id 1 add access_id 1 ip source_ip 10.42.73.1 port 1 deny Here we use the profile_id 1 which was specified when the access profile was created. The add parameter instructs the Switch to add the criteria that follows to the list of rules that are associated with access profile 1. For each rule entered into the access profile, you can assign an access_id that both identifies the rule and establishes a priority within the list of rules. A lower access_id gives the rule a higher priority. In case of a conflict in the rules entered for an access profile, the rule with the highest priority (lowest access_id) will take precedence. The ip parameter instructs the Switch that this new rule will be applied to the IP addresses contained within each frame's header. source_ip tells the Switch that this rule will apply to the source IP addresses in each frame's header. Finally, the IP address 10.42.73.1 will be combined with the source_ip_mask 255.255.255.0 to give the IP address 10.42.73.0 for any source IP address between 10.42.73.0 to 10.42.73.255. In the example used above - config access_profile profile_id 1 add access_id 1 ip source_ip 10.42.73.1 port 7 deny - a single access rule was created. This rule will subtract one rule available for the port group 1 - 8, as well as one rule from the total available rules. In order to address this functional limitation of the chip set, an additional function, CPU Interface Filtering, has been added. CPU Filtering may be universally enabled or disabled. Setting up CPU Interface Filtering follows the same syntax as ACL configuration and requires some of the same input parameters. To configure CPU Interface Filtering, see the descriptions below for create cpu access_profile and config cpu access_profile. To enable CPU Interface Filtering, see config cpu_interface_filtering. The xStack DES-3800 switch series has three ways of creating access profile entries on the Switch which include Ethernet (MAC Address), IP, and Packet Content. Due to the present complexity of the access profile commands, it has been decided to split this command into three pieces to be better understood by the user and therefore simpler for the user to configure. The beginning of this section displays the create access_profile and config access_profile commands in their entirety. The following table divides these commands up into the defining features necessary to properly configure the access profile. Remember these are not the total commands but the easiest way to implement Access Control Lists for the Switch. Command Parameters create access_profile [ethernet {vlan | source_mac | destination_mac | 802.1p | ethernet_type} profile_id ] config access_profile profile_id [add access_id [auto_assign | ] [ethernet {vlan | source_mac | destination_mac | 802.1p | ethernet_type } port [permit {priority {replace_priority} | deny | mirror] delete ] create access_profile ip [vlan | source_ip_mask | destination_ip_mask | dscp | [icmp {type | code} | igmp {type} | tcp {src_port_mask | dst_port_mask | flag_mask [all | {urg | ack | psh | rst | syn | fin}]} | udp {src_port_mask | dst_port_mask } | protocol_id {user _mask }]} profile_id ] config access_profile profile_id [add access_id [auto_assign | ] ip {vlan | source_ip | destination_ip | dscp | [icmp {type | code } | igmp {type } | tcp {src_port | dst_port | urg | ack | psh | rst | syn | fin} | udp {src_port | dst_port } | protocol_id {user_define }]} port [permit {priority {replace_priority} | replace_dscp } | deny | mirror] delete ] create access_profile packet_content_mask {offset_0-15 | offset_16-31 | offset_32-47 | offset_48-63 | offset_64-79 } profile_id } config access_profile profile_id [add access_id [auto_assign | ] packet_content {offset_0-15 | offset_16-31 | offset_32-47 | offset_48-63 146