D-Link DES-3828 Product Manual - Page 246
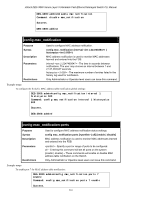
SSH Commands, Purpose, Syntax, enable ssh, Description, Parameters, Restrictions
 |
UPC - 790069276811
View all D-Link DES-3828 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 246 highlights
xStack DES-3800 Series Layer 3 Stackable Fast Ethernet Managed Switch CLI Manual 37 SSH COMMANDS The steps required to use the Secure Shell (SSH) protocol for secure communication between a remote PC (the SSH Client) and the Switch (the SSH Server), are as follows: 1. Create a user account with admin-level access using the create account admin command. This is identical to creating any other admin-lever user account on the Switch, including specifying a password. This password is used to login to the Switch, once secure communication has been established using the SSH protocol. 2. Configure the user account to use a specified authorization method to identify users that are allowed to establish SSH connections with the Switch using the config ssh user authmode command. There are three choices as to the method SSH will use to authorize the user, and they are password, publickey and hostbased. 3. Configure the encryption algorithm that SSH will use to encrypt and decrypt messages sent between the SSH Client and the SSH Server. 4. Finally, enable SSH on the Switch using the enable ssh command. After following the above steps, you can configure an SSH Client on the remote PC and manage the Switch using secure, in-band communication. The Secure Shell (SSH) commands in the Command Line Interface (CLI) are listed (along with the appropriate parameters) in the following table. Command Parameters enable ssh disable ssh config ssh authmode [password | publickey | hostbased] [enable | disable] show ssh authmode config ssh server {maxsession | contimeout | authfail | rekey [10min | 30min | 60min | never] show ssh server config ssh user authmode [hostbased [hostname | hostname_IP ] | password | publickey] show ssh user authmode config ssh algorithm [3DES | AES128 | AES192 | AES256 | arcfour | blowfish | cast128 | twofish128 | twofish192 | twofish256 | MD5 | SHA1 | RSA | DSA] [enable | disable] show ssh algorithm config ssh regenerate hostkey Each command is listed, in detail, in the following sections. enable ssh Purpose Syntax Description Parameters Restrictions Used to enable SSH. enable ssh This command allows you to enable SSH on the Switch. None. Only Administrator or Operator-level users can issue this command. Usage example: To enable SSH: 242