D-Link DFL-260 Product Manual - Page 347
Action, Src Iface, Src Net, Dest Iface, Dest Net, Parameters
 |
UPC - 790069296802
View all D-Link DFL-260 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 347 highlights
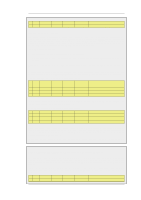
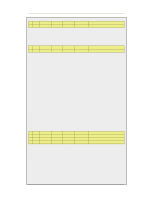
7.4.1. Translation of a Single IP Address (1:1) Chapter 7. Address Translation # Action Src Iface 2 Allow any Src Net all-nets Dest Iface core Dest Net wan_ip Parameters http These two rules allow us to access the web server via the NetDefend Firewall's external IP address. Rule 1 states that address translation can take place if the connection has been permitted, and rule 2 permits the connection. Of course, we also need a rule that allows internal machines to be dynamically address translated to the Internet. In this example, we use a rule that permits everything from the internal network to access the Internet via NAT hide: # Action Src Iface 3 NAT lan Src Net lannet Dest Iface any Dest Net all-nets Parameters All The problem with this rule set is that it will not work at all for traffic from the internal network. In order to illustrate exactly what happens, we use the following IP addresses: • wan_ip (195.55.66.77): a public IP address • lan_ip (10.0.0.1): the NetDefend Firewall's private internal IP address • wwwsrv (10.0.0.2): the web servers private IP address • PC1 (10.0.0.3): a machine with a private IP address The order of events is as follows: • PC1 sends a packet to wan_ip to reach www.ourcompany.com: 10.0.0.3:1038 => 195.55.66.77:80 • NetDefendOS translates the address in accordance with rule 1 and forwards the packet in accordance with rule 2: 10.0.0.3:1038 => 10.0.0.2:80 • wwwsrv processes the packet and replies: 10.0.0.2:80 => 10.0.0.3:1038 This reply arrives directly to PC1 without passing through the NetDefend Firewall. This causes problems. The reason this will not work is because PC1 expects a reply from 195.55.66.77:80 and not 10.0.0.2:80. The unexpected reply is discarded and PC1 continues to wait for a response from 195.55.66.77:80 which will never arrive. Making a minor change to the rule set in the same way as described above, will solve the problem. In this example, for no particular reason, we choose to use option 2: # Action 1 SAT 2 NAT 3 Allow Src Iface any lan any Src Net all-nets lannet all-nets Dest Iface core any core Dest Net wan_ip all-nets wan_ip Parameters http SETDEST wwwsrv 80 All http • PC1 sends a packet to wan_ip to reach "www.ourcompany.com": 10.0.0.3:1038 => 195.55.66.77:80 • NetDefendOS address translates this statically in accordance with rule 1 and dynamically in accordance with rule 2: 10.0.0.1:32789 => 10.0.0.2:80 • wwwsrv processes the packet and replies: 10.0.0.2:80 => 10.0.0.1:32789 • The reply arrives and both address translations are restored: 195.55.66.77:80 => 10.0.0.3:1038 In this way, the reply arrives at PC1 from the expected address. 347