Gateway ZX6800 Gateway Desktop Quick Start Guide - Page 31
Pay attention to privacy policies on Web sites and in software., Guard your email address., Start - review
 |
View all Gateway ZX6800 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 31 highlights
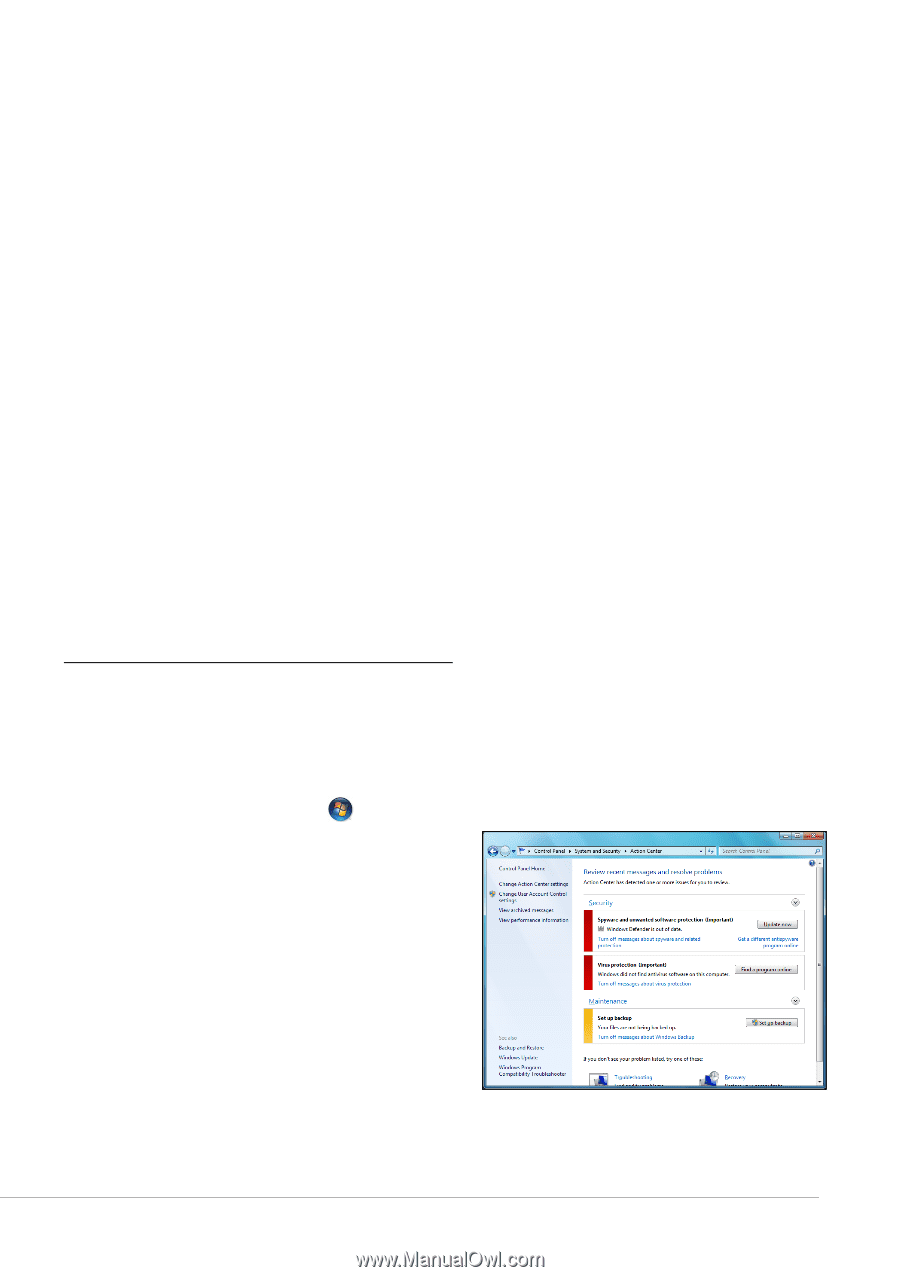
✓ Pay attention to privacy policies on Web sites and in software. It is important to understand how an organization might collect and use your personal information before you share it with them. ✓ Guard your email address. Spammers and phishers sometimes send millions of messages to email addresses that may or may not exist in hopes of finding a potential victim. Responding to these messages or even downloading images ensures you will be added to their lists for more of the same messages in the future. Also be careful when posting your email address online in newsgroups, blogs or online communities. Online offers that look too good to be true usually are. The old saying "there's no such thing as a free lunch" still rings true today. Supposedly "free" software such as screen savers or smileys, secret investment tricks sure to make you untold fortunes, and contests that you've surprisingly won without entering are the enticing hooks used by companies to grab your attention. While you may not directly pay for the software or service with money, the free software or service you asked for may have been bundled with advertising software ("adware") that tracks your behavior and displays unwanted advertisements. You may have to divulge personal information or purchase something else in order to claim your supposed content winnings. If an offer looks so good it's hard to believe, ask for someone else's opinion, read the fine print, or even better, simply ignore it. Review bank and credit card statements regularly. The impact of identity theft and online crimes can be greatly reduced if you can catch it shortly after your data is stolen or when the first use of your information is attempted. One of the easiest ways to get the tip-off that something has gone wrong is by reviewing the monthly statements provided by your bank and credit card companies for anything out of the ordinary. Additionally, many banks and services use fraud prevention systems that call out unusual purchasing behavior (i.e. if you live in Texas and all of the sudden start buying refrigerators in Budapest). In order to confirm these out of the ordinary purchases, they might call you and ask you to confirm them. Don't take these calls lightly; this is your hint that something bad may have happened and you should take necessary action. Protect your computer with Windows security tools. Windows provides a variety of protection applications. Windows Action Center Windows provides a central area from where you can control the security settings of your computer, helping you to protect it from Internet attacks and ensuring that the latest security updates have been downloaded and installed on your computer. To open the Action Center, click on Start > Control Panel > System and Security > Action Center. Alternatively, if a security alert has been reported (in the Notification Area, next to the clock) then you can click on the notification balloon or double-click on the small Security Alert icon. The Action Center indicates the status and settings used for important applications that protect your computer. In addition Windows Firewall, Windows Defender and Windows Automatic Updates are provided by Microsoft as part of a comprehesive system to defend your computer. The antivirus application varies according to the program installed on your computer. Helpdesk - 31