HP 4200n HP Jetdirect Print Servers - Administrator Guide - Page 184
Security Features 184, IP Access Control List, Telnet Control, Authentication and Encryption
 |
UPC - 808736313971
View all HP 4200n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 184 highlights
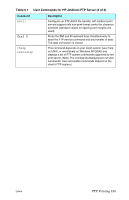
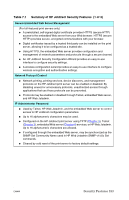
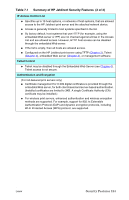
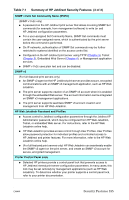
Table 7.1 Summary of HP Jetdirect Security Features (2 of 3) IP Access Control List G Specifies up to 10 host systems, or networks of host systems, that are allowed access to the HP Jetdirect print server and the attached network device. G Access is generally limited to host systems specified in the list. G By factory default, host systems that use HTTP (for example, using the embedded Web server or IPP) are not checked against entries in the Access List and are allowed access. However, HTTP host access can be disabled through the embedded Web server. G If the list is empty, then all hosts are allowed access. G Configured on the HP Jetdirect print server using TFTP (Chapter 3), Telnet (Chapter 3), embedded Web server (Chapter 4), or management software. Telnet Control G Telnet may be disabled through the Embedded Web Server (see Chapter 4). Telnet access is not secure. Authentication and Encryption (For full-featured print servers only) G Certificate management for X.509 digital certificates is provided through the embedded Web server, for both client-based and server-based authentication. (Installed certificates are limited to 3KB. A single Certificate Authority (CA) certificate may be installed.) G For wireless print servers, enhanced authentication and wireless encryption methods are supported. For example, support for 802.1x Extensible Authentication Protocol (EAP) and dynamic encryption protocols, including Wi-Fi Protected Access (WPA) protocol, are supported. ENWW Security Features 184