HP 510X HP Jetdirect Security Guidelines
HP 510X - JetDirect Print Server Manual
 |
UPC - 882780451322
View all HP 510X manuals
Add to My Manuals
Save this manual to your list of manuals |
HP 510X manual content summary:
- HP 510X | HP Jetdirect Security Guidelines - Page 1
HP Jetdirect?...4 Upgrading ...5 HP Jetdirect Administrative Guidelines 6 HP Jetdirect Hacks: TCP Port 9100...7 HP Jetdirect Hacks: Password and SNMP Community Names 9 HP Jetdirect Hacks: Firmware Upgrade 9 HP Jetdirect Hacks: Sniffing Print Jobs and Replaying Them 10 HP Jetdirect Hacks: Printer - HP 510X | HP Jetdirect Security Guidelines - Page 2
one of the first print servers to widely implement security protocols such as SSL/TLS, SNMPv3, 802.1X, and IPsec. If you are new to much as Ethernet. During this growth period in network printing, functionality within HP Jetdirect was designed to promote 'Ease-of-Use', to reduce support calls, and - HP 510X | HP Jetdirect Security Guidelines - Page 3
remains in use to this day: Use a smart networking card to implement the various networking infrastructure components to convert encapsulated network data into data for printer consumption. Thus, the HP Jetdirect was born - one of the first Networking Protocol offload engines. Let's refer to Figure - HP 510X | HP Jetdirect Security Guidelines - Page 4
Jetdirect J3258A 170x External Print Server Microsoft Windows 2000 Professional HP Jetdirect J4169A 610n EIO Print Server Microsoft Windows XP HP Jetdirect J6057A 615n EIO Print Server Microsoft Windows 2003 Server HP Jetdirect J7934A 620n EIO Print Server HP Jetdirect J7961A 635n EIO Print Server - HP 510X | HP Jetdirect Security Guidelines - Page 5
Embedded Jetdirect 10/100 (not for sale individually, comes installed on the formatter for certain printers/MFP devices) J7997G 630n EIO 10/100/1000 Print Server J7961G 635n EIO 10/100/1000 IPv6/IPsec Print Server Security Features Non-Cryptographic Security, not upgradeable to newer firmware after - HP 510X | HP Jetdirect Security Guidelines - Page 6
to install a J7961G 635n IPv6/IPsec print server. Using this product, we can take an older printer like the HP LaserJet 4000 and give it the latest in networking protocol and security support. This flexibility will come in handy as we evaluate the various attacks employed against HP Jetdirect and - HP 510X | HP Jetdirect Security Guidelines - Page 7
/100 Print Server J7960A/J7960G 625n EIO 10/100/1000 Print Server J7961A/J7961G 635n EIO 10/100/1000 IPv6/IPsec Print Server Firmware Version V.33.14/V.33.15 K.08.49 K.08.49 G.08.49 G.08.49 G.08.49 L.25.57 R.25.57 H.08.60 J.08.60 J.08.60 V.28.22 V.29.20 V.29.29 V.36.11 Table 4 - Jetdirect Firmware - HP 510X | HP Jetdirect Security Guidelines - Page 8
using the Firewall Option 3) For SET 4. Setup a rule to protect print traffic using IPsec Option 1) For Set 1/2/3/4. Setup an access control list for the network ID assigned to your company. As an example, for HP's internal network, there would be two entries: IP - 15.0.0.0 mask - 255.0.0.0 and - HP 510X | HP Jetdirect Security Guidelines - Page 9
partition and regain full functionality without having to contact HP support. There are three common ways of updating HP Jetdirect firmware: • HP Download Manager / HP Web Jetadmin • FTP • Embedded Web Server When using HP Download Manager or HP Web Jetadmin, the application issues an SNMP SET to - HP 510X | HP Jetdirect Security Guidelines - Page 10
file that was sent between an email client and email server, it can use Adobe Acrobat Reader to open it. printer/MFP's PJL library over a print connection. These tools often claim to bypass HP Jetdirect security. However, as we've seen from our functional diagram, HP Jetdirect controls the networking - HP 510X | HP Jetdirect Security Guidelines - Page 11
TFTP configuration file: picasso.cfg under the subdirectory of "hpnp" of the TFTP daemon's home directory • Forces HP Jetdirect to remain with BOOTP and not transition to DHCP if a BOOTP server is unavailable. An example of the contents of the TFTP configuration file picasso.cfg: # Allow subnet 192 - HP 510X | HP Jetdirect Security Guidelines - Page 12
a parameter file called "pjlprotection". This file is sent to the printer on power-up. Here is a sample content for the pjlprotection HP Jetdirect products that are in SET 2, the security wizard is recommended for non HP Web Jetadmin users. The security wizard can be access via the Networking tab - HP 510X | HP Jetdirect Security Guidelines - Page 13
First and foremost, set a password. 13 - HP 510X | HP Jetdirect Security Guidelines - Page 14
Change the Encryption Strength to "Medium" and check the "Encrypt All Web Communication " checkbox. This checkbox forces HTTPS to be used for all web communication. Uncheck "Enable Telnet and FTP Firmware Update" and "Enable RCFG". 14 - HP 510X | HP Jetdirect Security Guidelines - Page 15
Uncheck "Enable SNMPv1/v2" and check Enable "SNMPv3". Provide SNMPv3 parameters. 15 - HP 510X | HP Jetdirect Security Guidelines - Page 16
Based upon the customer's environment, read only SNMPv1/v2c access may need to be granted. Some tools such as the HP Standard Port Monitor use SNMPv1/v2c for status. Setup an Access Control List entry. This is another customer environment specific entry. In this example, the - HP 510X | HP Jetdirect Security Guidelines - Page 17
Disable unused print protocols and services. Allowing device discovery helps in device management, but may not be required in all environments. 802.1X authentication can also be done. Special equipment is required. For a complete discussion of 802.1X, see HP Jetdirect whitepapers on the topic. For - HP 510X | HP Jetdirect Security Guidelines - Page 18
Configuration Review Configuration review. Click "Finish" to set the configuration. Recommended Security Deployments: SET 3 First and foremost, SET 3 configuration needs to have the Security Wizard for SET 2 executed. Once - HP 510X | HP Jetdirect Security Guidelines - Page 19
page. Select the drop down box for the Default Rule to be "Allow" and then click "Add Rules..." We have a specific administrator subnet defined for printing and imaging devices. Click the "New" button so we can be very specific about what addresses can manage the device. 19 - HP 510X | HP Jetdirect Security Guidelines - Page 20
We'll define the IPv4 address range first. Select "All IPv4 Addresses" for Local Address and then we specified the 192.168.0/24 subnet for the Remote Address. We've also named this address template very clearly. Now for IPv6. Click "New" again. NOTE: If IPv6 is not used on your network, go to TCP/IP - HP 510X | HP Jetdirect Security Guidelines - Page 21
Select the appropriate IPv6 addresses and name the address template. Now that we have the address templates, let's create a rule. Rules are processed in priority order from 1 - 10. Let's create an IPv4 rule first. Select the IPv4 address template you created, then click "Next". 21 - HP 510X | HP Jetdirect Security Guidelines - Page 22
We are concerned with management services, so select the service template "All Jetdirect Management Services". Click "Next". Select "Allow Traffic". Click "Next" 22 - HP 510X | HP Jetdirect Security Guidelines - Page 23
Select "Create another rule". Select the IPv6 address template you created and then click "Next". 23 - HP 510X | HP Jetdirect Security Guidelines - Page 24
Select the "All Jetdirect Management Services" service template. Click "Next". Select "Allow Traffic". Click Next. 24 - HP 510X | HP Jetdirect Security Guidelines - Page 25
We have allowed management traffic from our IPv4/IPv6 administrative subnet. Now we must create a rule to throw away all other management traffic. Click "Create another rule". Here we select "All IP addresses" which encompasses both IPv4 and IPv6. Click "Next". 25 - HP 510X | HP Jetdirect Security Guidelines - Page 26
Again, select "All Jetdirect Management Services" for the service template and then click "Next". Select "Drop". Click "Next". 26 - HP 510X | HP Jetdirect Security Guidelines - Page 27
our policy. Rules are processed from 1 to 10. If a packet comes from or is going to our defined IPv4/IPv6 subnet, the rule will match and it will be allowed. Otherwise, if it is a management service, it will be dropped. All other traffic will be allowed (the default rule is allow). Click "Finish - HP 510X | HP Jetdirect Security Guidelines - Page 28
did with SET 3, only this time, we'll simply say that all IP addresses must use IPsec to utilize a management protocol. If an end station tries to communicate with a management protocol to Jetdirect without using IPsec, the packets are dropped by the IP layer. Be sure that you are using HTTPS before - HP 510X | HP Jetdirect Security Guidelines - Page 29
Select "All Jetdirect Management Services". Click "Next". Select "Require traffic to be protected with an IPsec/Firewall Policy". Click "Next". 29 - HP 510X | HP Jetdirect Security Guidelines - Page 30
Click "New". Name the IPsec Template. Some Jetdirect models may require you to configure IKE parameters. However, this model has a quick set of IKE defaults that can be used. The one selected is for more emphasis on Interoperability and less on Security. Click "Next". 30 - HP 510X | HP Jetdirect Security Guidelines - Page 31
For example purposes only, Pre-Shared Key Authentication is used. HP does not recommend using PreShared Key Authentication. Certificates or Kerberos is highly recommended. Click "Next". Select the IPsec template you just created. Click "Next". 31 - HP 510X | HP Jetdirect Security Guidelines - Page 32
Here is our IPsec policy. If a management protocol is to be used, it must use IPsec. All other traffic is allowed based upon the default rule. Click "Finish". Select "Yes" to enable the IPsec policy. You can also choose to have a failsafe if you would like. Click "OK". 32 - HP 510X | HP Jetdirect Security Guidelines - Page 33
.pdf IPsec: http://h20000.www2.hp.com/bc/docs/support/SupportManual/c01048192/c01048192.pdf IPv6: http://h20000.www2.hp.com/bc/docs/support/SupportManual/c00840100/c00840100.pdf Using the networking infrastructure to better protect your printing and imaging devices: http://h20000.www2.hp.com

HP Jetdirect Security Guidelines
whitepaper
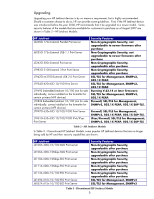
Table of Contents:
Introduction
.....................................................................................................................................
1
HP Jetdirect Overview
......................................................................................................................
2
What is an HP Jetdirect?
...................................................................................................................
3
How old is Your HP Jetdirect?
............................................................................................................
4
Upgrading
......................................................................................................................................
5
HP Jetdirect Administrative Guidelines
................................................................................................
6
HP Jetdirect Hacks: TCP Port 9100
.....................................................................................................
7
HP Jetdirect Hacks: Password and SNMP Community Names
................................................................
9
HP Jetdirect Hacks: Firmware Upgrade
...............................................................................................
9
HP Jetdirect Hacks: Sniffing Print Jobs and Replaying Them
.................................................................
10
HP Jetdirect Hacks: Printer/MFP access
............................................................................................
10
Recommended Security Deployments: SET 1
......................................................................................
11
Recommended Security Deployments: SET 2
......................................................................................
12
Recommended Security Deployments: SET 3
......................................................................................
18
Recommended Security Deployments: SET 4
......................................................................................
28
Further Reading
.............................................................................................................................
33
Introduction
The availability of public information on the Internet for hacking HP Jetdirect products has prompted
customers to ask HP about how they can protect their printing and imaging devices against such
attacks and what is HP doing about preventing those attacks.
In all fairness, some of this public
information is of rather poor quality and inflammatory; however, some websites detailing the attacks
and the vulnerabilities on HP Jetdirect are informative and raise valid concerns that need to be
addressed.
It is the purpose of this whitepaper to address customer concerns about these attacks and
vulnerabilities and to recommend proper security configurations to help customers protect their
printing and imaging devices.
This whitepaper is only a small part of a broad initiative within HP to
educate our customer base about printing and imaging security.
Resources such as The Secure
Printing website (
) provide a great deal of information for
customers about products, solutions, as well as configuration recommendations. In general, a lot of
this information can be put to use on existing HP Jetdirect products, mainly because HP Jetdirect was
1