HP Pavilion m6-1000 User Guide - Page 78
Securing your wireless network, Backing up your software applications and information, Using an
 |
View all HP Pavilion m6-1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 78 highlights
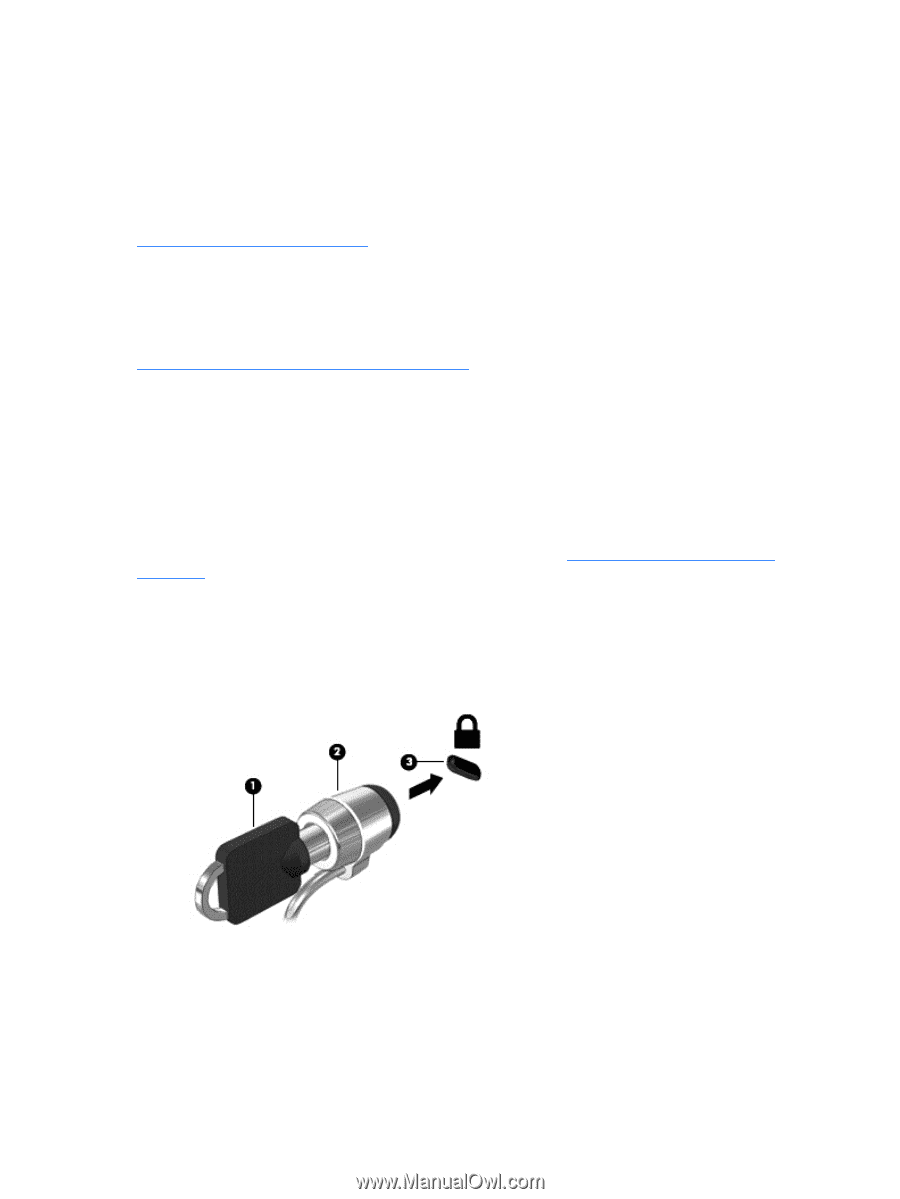
If you have installed third-party software after you purchased your computer, regularly update the software. Software companies provide software updates to their products to correct security problems and improve functionality of the software. Securing your wireless network When you set up your wireless network, always enable security features. For more information, see Protecting your WLAN on page 20. Backing up your software applications and information Regularly back up your software applications and information to protect them from being permanently lost or damaged through a virus attack or a software or hardware failure. For more information, see Backing up, restoring, and recovering on page 72. Using an optional security cable lock A security cable lock, which is purchased separately, is designed to act as a deterrent, but it may not prevent the computer from being mishandled or stolen. Security cable locks are only one of several methods that should be employed as part of a complete security solution to help maximize theft protection. The security cable slot on your computer may look slightly different from the illustration in this section. For the location of the security cable slot on your computer, see Getting to know your computer on page 4. 1. Loop the security cable lock around a secured object. 2. Insert the key (1) into the security cable lock (2). 3. Insert the security cable lock into the security cable slot on the computer (3), and then lock the security cable lock with the key. 4. Remove the key and keep it in a safe place. 68 Chapter 9 Securing your computer and information