Konica Minolta bizhub 223 bizhub 223/283/363/423 PKI Security Operations User - Page 50
User Authentication Function
 |
View all Konica Minolta bizhub 223 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 50 highlights
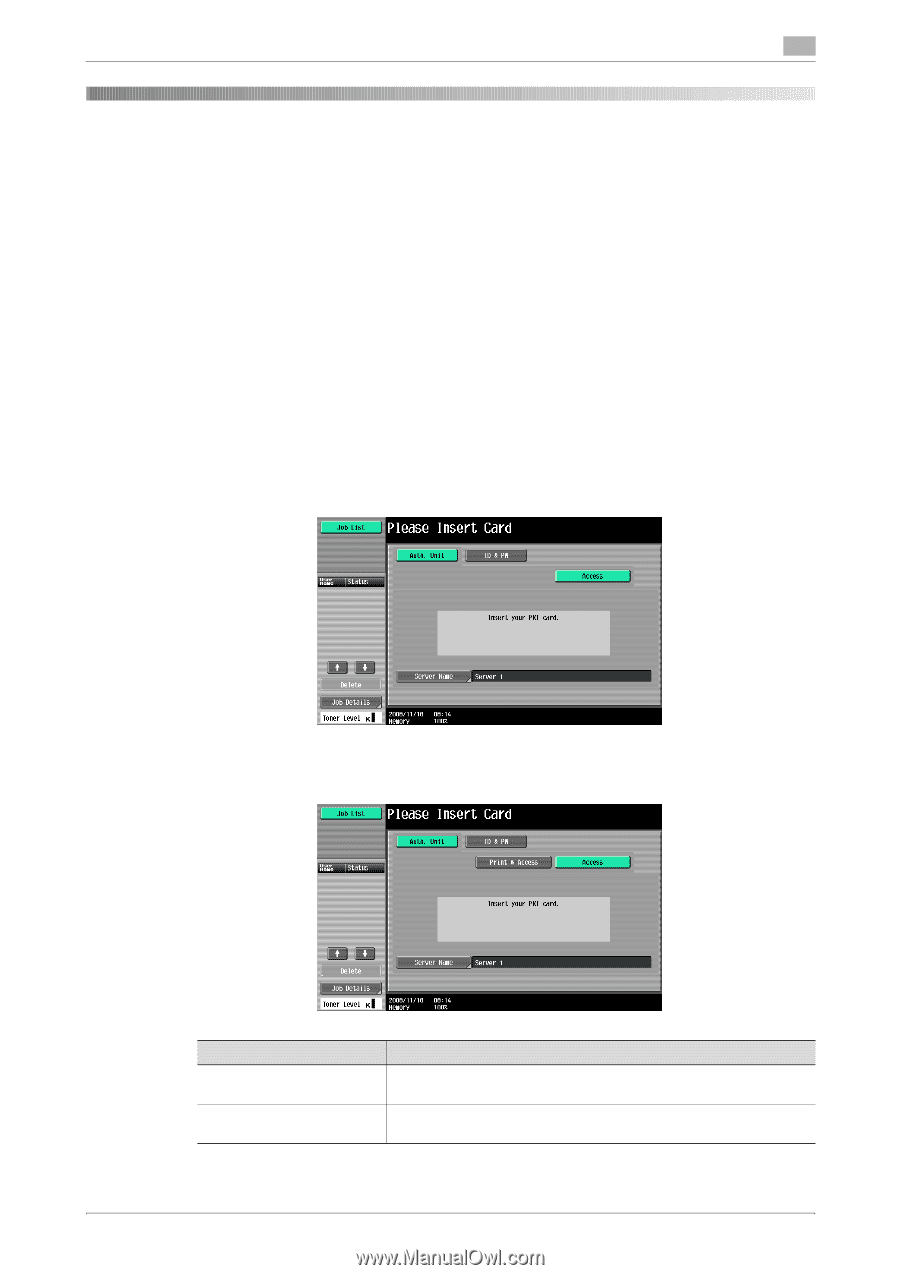
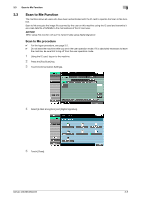
3.1 User Authentication Function 3 3 User Operations 3.1 User Authentication Function To authenticate a user before he or she actually uses the machine, user authentication is performed using the IC card and PIN code. The IC card reader installed in the machine is used to read the IC card. The PIN code entered is displayed as "*" during the authentication procedure. If a document is saved in the PKI Encrypted Document User Box of this machine, the print data of the user in question saved in the PKI Encrypted Document User Box of this machine can be automatically printed after the authentication by means of the IC card on the control panel is successful. Because printing occurs after user authentication is performed via the control panel of this machine, it is suitable for printing highly confidential documents. User authentication using the IC card 0 Contact the Administrator of the machine if the server is not registered. 0 Do not leave the machine while you are in the user operation mode. If it is absolutely necessary to leave the machine, be sure first to log off from the user operation mode. 1 Insert the IC card into the IC card reader connected to the machine. % The following screen appears if any document is saved in the PKI Encrypted Document User Box. After selecting [Print & Access] or [Access], insert the IC card into the IC card reader. Login Method Description [Print & Access] The user operation mode screen is called to the screen after the PKI Encrypted document of the corresponding user is printed. [Access] Only the ordinary login procedure is applicable and no PKI Encrypted document are printed. % If there are two or more PKI Encrypted documents are involved, all of them will be printed. To select and print only a specific document, select [Access] and select the specific document from those in bizhub 423/363/283/223 3-2