Kyocera KM-1820 Fax System (K) Operation Guide - Page 130
Encrypted Communication, Decryption
 |
View all Kyocera KM-1820 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 130 highlights
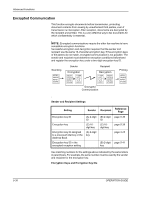
Advanced Functions Encrypted Communication This function encrypts documents before transmission, protecting document contents from viewing by unauthorized third parties, even if transmission is intercepted. After reception, documents are decrypted by the recipient and printed. This is a very effective way to fax documents for which confidentiality is essential. NOTE: Encrypted communications require the other fax machine to have compatible encryption functions. Successful encryption and decryption requires that the sender and recipient use the same 16-character encryption key. If the encryption keys of the parties do not match, encrypted communication is not possible. The sender and recipient must determine encryption conditions beforehand and register the encryption key under a two-digit encryption key ID. Scanning Sender Encryption Recipient Decryption Printing Encrypted Communication Sender and Recipient Settings Setting Sender Recipient Reference Page Encryption key ID (A) 2-digit (B) 2-digit page 5-39 ID ID Encryption key (C) 16digit key (C) 16digit key page 5-39 Encryption key ID assigned to a one-touch dial key or the Address Book (A) 2-digit key page 3-25 Encryption key ID in the encrypted reception setting (B) 2-digit page 5-41 key Use matching numbers for the settings above indicated by the same letters in parenthesis. For example, the same number must be used by the sender and recipient for the encryption key. Encryption Keys and Encryption Key IDs 5-38 OPERATION GUIDE