Lenovo ThinkPad L520 (English) User Guide - Page 165
Function, Selection, Comments, Enabled, I/O Port Access, Memory Card Slot
 |
View all Lenovo ThinkPad L520 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 165 highlights
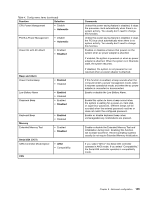
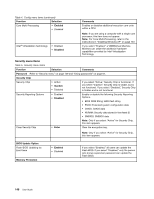
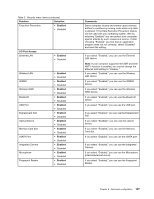
Table 5. Security menu items (continued) Function Selection Execution Prevention • Enabled • Disabled I/O Port Access Ethernet LAN Wireless LAN WiMAX Wireless WAN Bluetooth USB Port ExpressCard Slot Optical Device Memory Card Slot eSATA Port Integrated Camera Microphone Fingerprint Reader • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled • Enabled • Disabled Comments Some computer viruses and worms cause memory buffers to overflow by running code where only data is allowed. If the Data Execution Prevention feature can be used with your operating system, then by selecting "Enabled" you can protect your computer against attacks by such viruses and worms. If after choosing "Enabled" you find that an application program does not run correctly, select "Disabled" and reset the setting. If you select "Enabled," you can use the Ethernet LAN device. Note: If your computer supports Intel AMT and Intel AMT's function is enabled, you cannot change the Ethernet LAN setting to "Disable.," If you select "Enabled," you can use the Wireless LAN device. If you select "Enabled," you can use the WiMAX device. If you select "Enabled," you can use the Wireless WAN device. If you select "Enabled," you can use the Bluetooth device. If you select "Enabled," you can use the USB port. If you select "Enabled," you can use the ExpressCard Slot. If you select "Enabled," you can use the optical device. If you select "Enabled," you can use the Memory Card slot. If you select "Enabled," you can use the eSATA port. If you select "Enabled," you can use the Integrated Camera. If you select "Enabled," you can use the Microphone (Internal/External/Line-In). If you select "Enabled," you can use the Fingerprint Reader. Chapter 8. Advanced configuration 147