Netgear WG602v2 WG602v2 User Manual - Page 74
WPA Authentication: Enterprise-level User Authentication via 802.1x/EAP and RADIUS
 |
View all Netgear WG602v2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 74 highlights
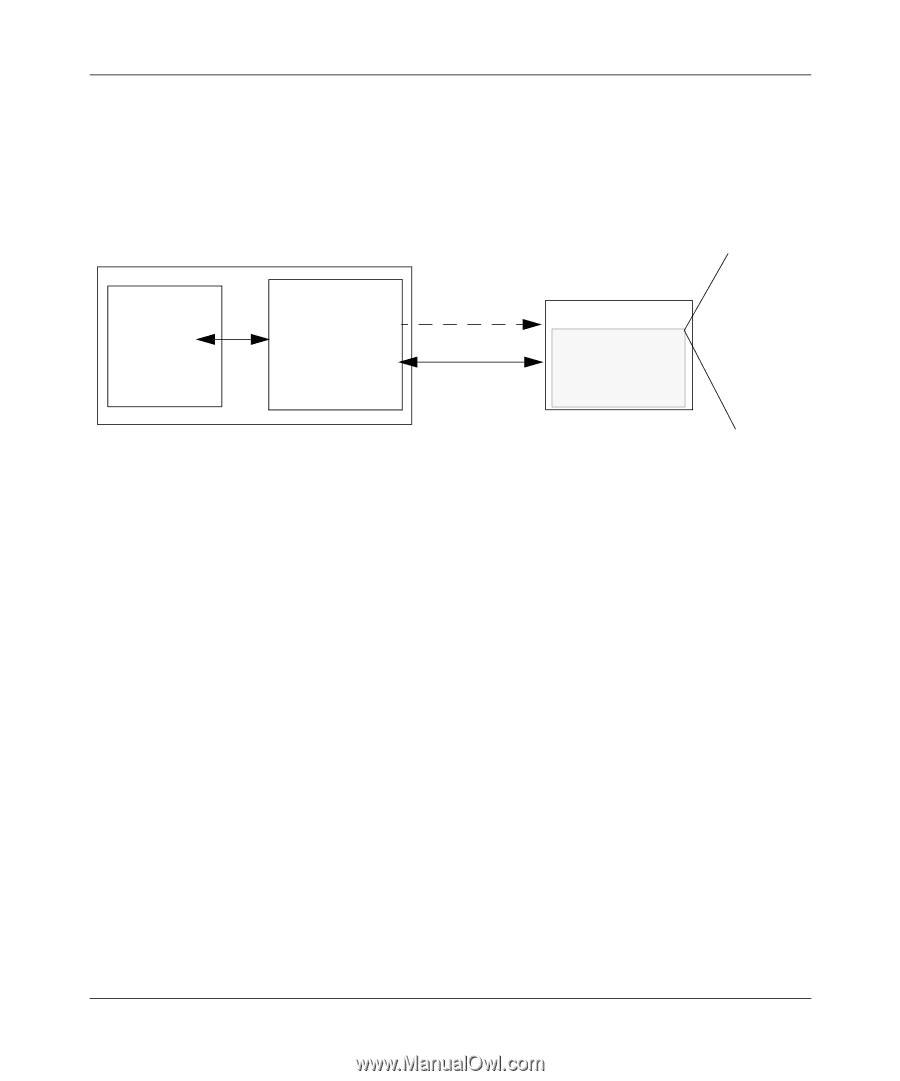
Reference Manual for the WG602 v2 54 Mbps Wireless Access Point WPA Authentication: Enterprise-level User Authentication via 802.1x/EAP and RADIUS Wireless LAN WPA enabled wireless client with "supplicant" WPA enabled Access Point using pre-shared key or 802.1x Figure B-3: WPA Overview Wired Network with Optional 802.1x Port Based Network Access Control TCP/IP Ports Closed Until TCP/IP Ports Opened After Authenticated RADIUS Server Login Authentication Optional Certificate Authority (eg Win Server, VeriSign, etc) IEEE 802.1x offers an effective framework for authenticating and controlling user traffic to a protected network, as well as providing a vehicle for dynamically varying data encryption keys via EAP from a RADIUS server, for example. This framework enables using a central authentication server, which employs mutual authentication so that a rogue wireless user does not join the network. It's important to note that 802.1x doesn't provide the actual authentication mechanisms. When using 802.1x, the EAP type, such as Transport Layer Security (EAP-TLS) or EAP Tunneled Transport Layer Security (EAP-TTLS) defines how the authentication takes place. Note: For environments with a Remote Authentication Dial-In User Service (RADIUS) infrastructure, WPA supports Extensible Authentication Protocol (EAP). For environments without a RADIUS infrastructure, WPA supports the use of a preshared key. Together, these technologies provide a framework for strong user authentication. Windows XP implements 802.1x natively, and several Netgear switch and wireless access point products support 802.1x. B-12 M-10181-03 Wireless Networking Basics