Oki C9600n OkiLAN 510w Glossary
Oki C9600n Manual
 |
View all Oki C9600n manuals
Add to My Manuals
Save this manual to your list of manuals |
Oki C9600n manual content summary:
- Oki C9600n | OkiLAN 510w Glossary - Page 1
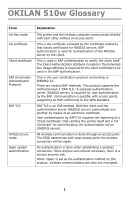
mode Open system authentication Explanation The printer and the wireless computer communicate is required for the client certificate to be used in the EAP authentication. This is the by the EAP. Communication is possible with access points supporting an EAP conforming to the WPA standard. EAP-TLS - Oki C9600n | OkiLAN 510w Glossary - Page 2
printer can only be done with an access point or wireless computer on which the same WEP key has been set. You must set the WEP key to use this method. SSID (Service Privacy) This is the basic wireless LAN encryption method. This product supports the 64 bit and 128 bit WEP key sizes. The same WEP
1
OKILAN 510w Glossary
Term
Explanation
Ad-Hoc mode
The printer and the wireless computer communicate directly
with each other without an access point.
CA certificate
This is the certificate provided by the Certificate Authority
that issues certificates for RADIUS servers. EAP
authentication is used for authentication of the RADIUS
server by the client.
Client certificate
This is used in EAP authentication to certify the client itself.
The Client Authentication attribute included in the Extended
Key Usage attribute is required for the client certificate to be
used in the EAP authentication.
EAP (Extensible
Authentication
Protocol)
This is the user certification protocol conforming to
IEEE802.1X.
There are various EAP methods. This product supports the
method known a ’EAP-TLS.’ A separate authentication
server (RADIUS server) is required for user authentication
by the EAP. Communication is possible with access points
supporting an EAP conforming to the WPA standard.
EAP-TLS
EAP-TLS is an EAP method. Both the client and the
authentication server (RADIUS server) authenticate one
another by means of an electronic certificate.
User authentication by EAP-TLS requires the importing of a
’Client Certificate’ that certifies the printer itself and a ’CA
Certificate’ for authenticating the authentication server
(RADIUS server).
Infrastructure
mode
All wireless communication is done through an access point.
The SSID determines with what access point the wireless
connection will be made.
Open system
authentication
No authentication is done when establishing a wireless
connection. Since anyone can connect wirelessly, there is a
serious security risk.
When ’Open’ is set as the authentication method on this
product, wireless communications are also not encrypted.