Samsung ML-2545 User Manual (user Manual) (ver.1.01) (English) - Page 65
Subnet Mask, TCP/IP, Toner Cartridge, TWAIN, UNC Path, Watermark, WPA-PSK
 |
View all Samsung ML-2545 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 65 highlights
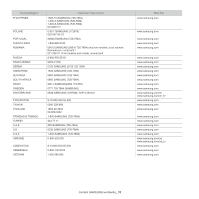
between nodes on a network. It also provides an authenticated Inter-process communication mechanism. SMTP Simple Mail Transfer Protocol (SMTP) is the standard for e-mail transmissions across the Internet. SMTP is a relatively simple, text-based protocol, where one or more recipients of a message are specified, and then the message text is transferred. It is a client-server protocol, where the client transmits an email message to the server. SSID Service Set Identifier (SSID) is a name of a wireless local area network (WLAN). All wireless devices in a WLAN use the same SSID in order to communicate with each other. The SSIDs are case-sensitive and have a maximum length of 32 characters. Subnet Mask The subnet mask is used in conjunction with the network address to determine which part of the address is the network address and which part is the host address. TCP/IP The Transmission Control Protocol (TCP) and the Internet Protocol (IP); the set of communications protocols that implement the protocol stack on which the Internet and most commercial networks run. TCR Transmission Confirmation Report (TCR) provides details of each transmission such as job status, transmission result and number of pages sent. This report can be set to print after each job or only after failed transmissions. TIFF Tagged Image File Format (TIFF) is a variable-resolution bitmapped image format. TIFF describes image data that typically come from scanners. TIFF images make use of tags, keywords defining the characteristics of the image that is included in the file. This flexible and platform-independent format can be used for pictures that have been made by various image processing applications. Toner Cartridge A kind of bottle or container used in a machine like a printer which contains toner. Toner is a powder used in laser printers and photocopiers, which forms the text and images on the printed paper. Toner can be fused by by a combination of heat/pressure from the fuser, causing it to bind to the fibers in the paper. TWAIN An industry standard for scanners and software. By using a TWAIN-compliant scanner with a TWAIN-compliant program, a scan can be initiated from within the program. It is an image capture API for Microsoft Windows and Apple Macintosh operating systems. UNC Path Uniform Naming Convention (UNC) is a standard way to access network shares in Window NT and other Microsoft products. The format of a UNC path is: \\\\ URL Uniform Resource Locator (URL) is the global address of documents and resources on the Internet. The first part of the address indicates what protocol to use, the second part specifies the IP address or the domain name where the resource is located. USB Universal Serial Bus (USB) is a standard that was developed by the USB Implementers Forum, Inc., to connect computers and peripherals. Unlike the parallel port, USB is designed to concurrently connect a single computer USB port to multiple peripherals. Watermark A watermark is a recognizable image or pattern in paper that appears lighter when viewed by transmitted light. Watermarks were first introduced in Bologna, Italy in 1282; they have been used by papermakers to identify their product, and also on postage stamps, currency, and other government documents to discourage counterfeiting. WEP Wired Equivalent Privacy (WEP) is a security protocol specified in IEEE 802.11 to provide the same level of security as that of a wired LAN. WEP provides security by encrypting data over radio so that it is protected as it is transmitted from one end point to another. WIA Windows Imaging Architecture (WIA) is an imaging architecture that is originally introduced in Windows Me and Windows XP. A scan can be initiated from within these operating systems by using a WIA-compliant scanner. WPA Wi-Fi Protected Access (WPA) is a class of systems to secure wireless (Wi-Fi) computer networks, which was created to improve upon the security features of WEP. WPA-PSK WPA-PSK (WPA Pre-Shared Key) is special mode of WPA for small business or home users. A shared key, or password, is configured in the wireless access point (WAP) and any wireless laptop or desktop devices. WPA-PSK generates a unique key for each session between a wireless client and the associated WAP for more advanced security. WPS The Wi-Fi Protected Setup (WPS) is a standard for establishing a wireless home network. If your wireless access point supports WPS, you can configure the wireless network connection easily without a computer. Glossary_ 65