ZyXEL P-660HW-T1 v2 User Guide - Page 153
Firewall Rules Summary
 |
View all ZyXEL P-660HW-T1 v2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 153 highlights
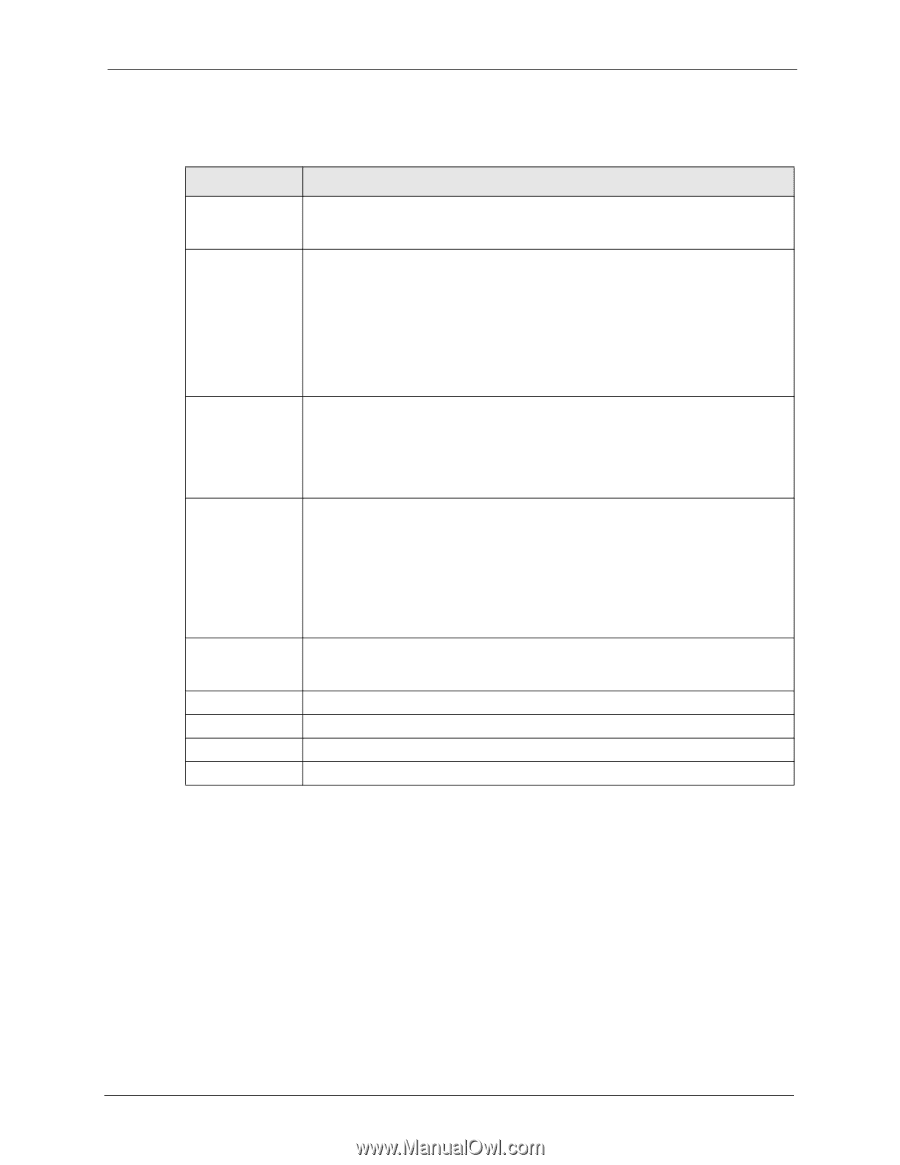
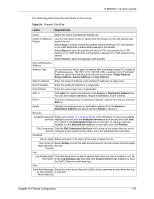
P-660HW-T v2 User's Guide The following table describes the labels in this screen. Table 52 Firewall: General LABEL Active Firewall Bypass Triangle Route DESCRIPTION Select this check box to activate the firewall. The ZyXEL Device performs access control and protects against Denial of Service (DoS) attacks when the firewall is activated. Select this check box to have the ZyXEL Device firewall permit the use of triangle route topology on the network. See the appendix for more on triangle route topology. Packet Direction Default Action Log Expand... Basic... Apply Cancel Note: Allowing asymmetrical routes may let traffic from the WAN go directly to a LAN computer without passing through the router. See Appendix M on page 343 for more on triangle route topology and how to deal with this problem. This is the direction of travel of packets (LAN to LAN / Router, LAN to WAN, WAN to WAN / Router, WAN to LAN). Firewall rules are grouped based on the direction of travel of packets to which they apply. For example, LAN to LAN / Router means packets traveling from a computer/subnet on the LAN to either another computer/subnet on the LAN interface of the ZyXEL Device or the ZyXEL Device itself. Use the drop-down list boxes to select the default action that the firewall is take on packets that are traveling in the selected direction and do not match any of the firewall rules. Select Drop to silently discard the packets without sending a TCP reset packet or an ICMP destination-unreachable message to the sender. Select Reject to deny the packets and send a TCP reset packet (for a TCP packet) or an ICMP destination-unreachable message (for a UDP packet) to the sender. Select Permit to allow the passage of the packets. Select the check box to create a log (when the above action is taken) for packets that are traveling in the selected direction and do not match any of your customized rules. Click this button to display more information. Click this button to display less information. Click Apply to save your changes to the ZyXEL Device. Click Cancel to begin configuring this screen afresh. 10.6 Firewall Rules Summary Note: The ordering of your rules is very important as rules are applied in turn. Refer to Section 9.1 on page 137 for more information. Click Security > Firewall > Rules to bring up the following screen. This screen displays a list of the configured firewall rules. Note the order in which the rules are listed. Chapter 10 Firewall Configuration 153