ZyXEL P-660HW-T1 v2 User Guide - Page 235
Table 100, Table 99
 |
View all ZyXEL P-660HW-T1 v2 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 235 highlights
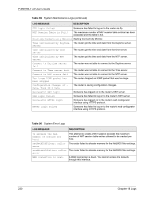
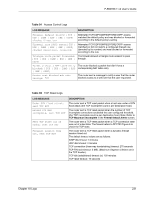
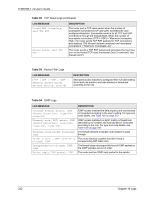
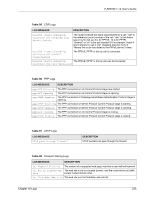
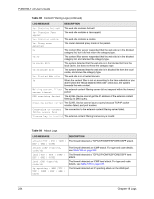
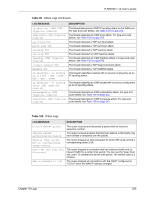
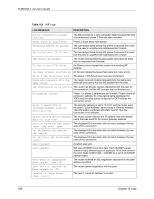
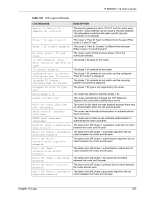
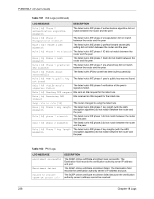
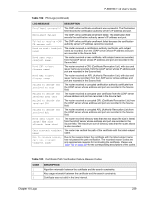
P-660HW-T v2 User's Guide Table 99 Attack Logs (continued) LOG MESSAGE DESCRIPTION ip spoofing - WAN ICMP (type:%d, code:%d) icmp echo: ICMP (type:%d, code:%d) syn flood TCP ports scan TCP teardrop TCP teardrop UDP teardrop ICMP (type:%d, code:%d) illegal command TCP NetBIOS TCP ip spoofing - no routing entry [TCP | UDP | IGMP | ESP | GRE | OSPF] ip spoofing - no routing entry ICMP (type:%d, code:%d) vulnerability ICMP (type:%d, code:%d) traceroute ICMP (type:%d, code:%d) The firewall detected an ICMP IP spoofing attack on the WAN port. For type and code details, see Table 106 on page 242. The firewall detected an ICMP echo attack. For type and code details, see Table 106 on page 242. The firewall detected a TCP syn flood attack. The firewall detected a TCP port scan attack. The firewall detected a TCP teardrop attack. The firewall detected an UDP teardrop attack. The firewall detected an ICMP teardrop attack. For type and code details, see Table 106 on page 242. The firewall detected a TCP illegal command attack. The firewall detected a TCP NetBIOS attack. The firewall classified a packet with no source routing entry as an IP spoofing attack. The firewall classified an ICMP packet with no source routing entry as an IP spoofing attack. The firewall detected an ICMP vulnerability attack. For type and code details, see Table 106 on page 242. The firewall detected an ICMP traceroute attack. For type and code details, see Table 106 on page 242. Table 100 IPSec Logs LOG MESSAGE DESCRIPTION Discard REPLAY packet The router received and discarded a packet with an incorrect sequence number. Inbound packet authentication failed The router received a packet that has been altered. A third party may have altered or tampered with the packet. Receive IPSec packet, but no corresponding tunnel exists The router dropped an inbound packet for which SPI could not find a corresponding phase 2 SA. Rule idle time out, disconnect The router dropped a connection that had outbound traffic and no inbound traffic for a certain time period. You can use the "ipsec timer chk_conn" CI command to set the time period. The default value is 2 minutes. WAN IP changed to The router dropped all connections with the "MyIP" configured as "0.0.0.0" when the WAN IP address changed. Chapter 18 Logs 235