Compaq ProLiant 1000 Architecting and Deploying High-Availability Solutions - Page 7
Vulnerable Technologies
 |
View all Compaq ProLiant 1000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 7 highlights
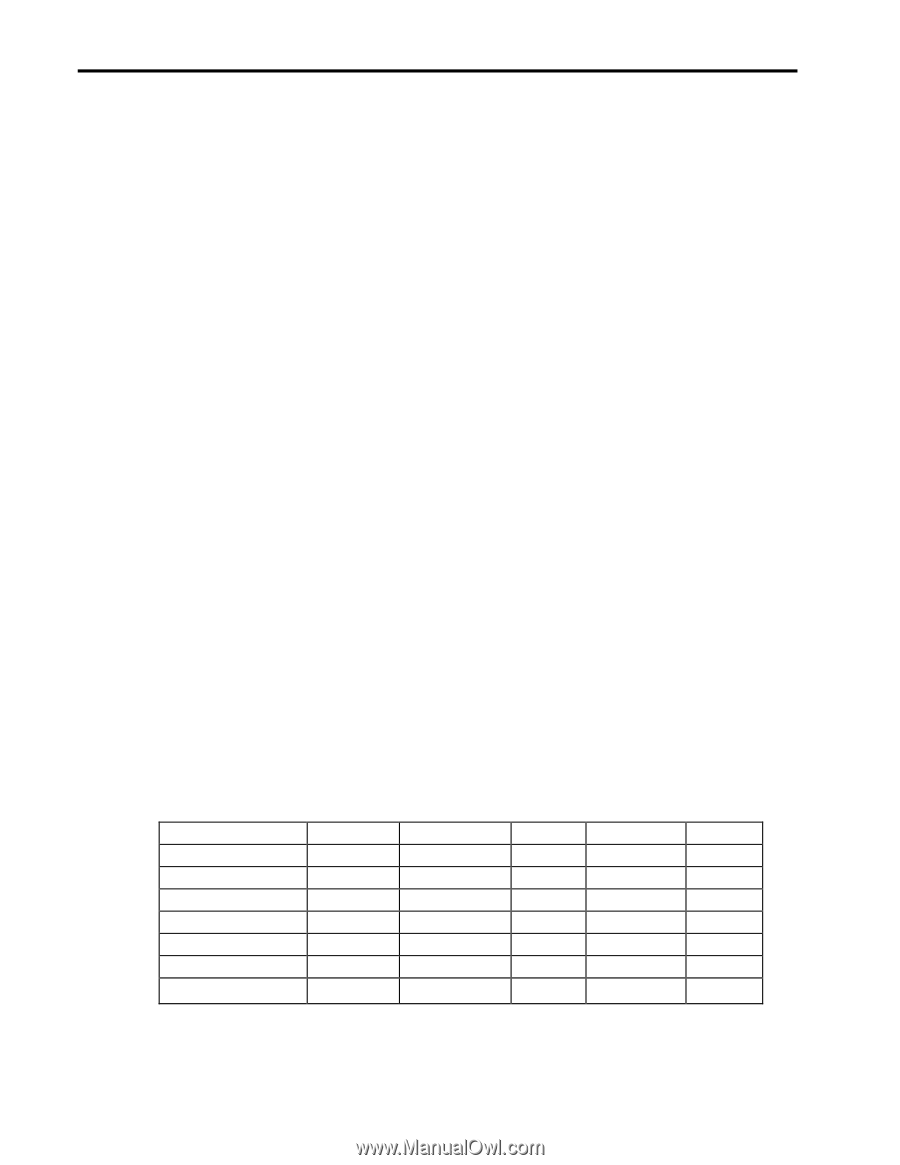
Architecting and Deploying High-Availability Solutions 7 4. Vulnerable Technologies Once you've looked at risk and cost, recovery, and failure events, you then need to turn your attention to the following technology areas. Hardware: Is the concern uninterruptible power supply, memory integrity, I/O, or processor failure? Operating system: Some operating systems tend to be more stable than others, nevertheless, problems do occur that can affect an operating system and cause it to corrupt a process. Once the operating system is in failure everything above it such as databases, applications, processes, and more can be lost. Storage: Is your business data-centric, transaction-centric, or both? If it is data-centric you do not want to lose what is in your storage system; you don't want to lose access to that vital data; and, perhaps worst of all, what happens if that data becomes corrupted? Database: Whether your business is data-centric or transaction-centric the loss or corruption of a database can spell disaster. This brings up the question about the need to replicate data. Network: Whether it is backing up data over wide-area connections, the high-speed connections needed for transaction processing, or the continuous availability of information already gathered, a robust network infrastructure is a foundation on which to build truly high-availability environments. Management: How much does it cost to manage this whole system? What happens if you are no longer able to deal with intrusions? How can you easily, or at least with minimum disruption, upgrade, expand, or tune your system to ensure that your enterprise operates at peak profitability? Application: Is the application always there for you? Can you upgrade it without taking your system down? Can the application take advantage of the underlying high-availability elements? Interdependencies are also a concern. Storage failure, for example, can corrupt a database leading to operating system hang-up. Looking at the Causes and Vulnerable Technologies Together Once you have gained an understanding of which causes of downtime are of most concern and which technologies are most at risk, you can begin to analyze your total environment and architect the highavailability system that is right for you. This can be done in-house or with the assistance of a third party. Compaq has considerable experience in this area and stands ready to assist you. Availability Matrix The matrix below is a simple yet effective way to quantify your availability requirements. The top row displays the locations where failure events occur and the leftmost column lists the technology areas that must be addressed to minimize the loss of availability. Hardware Operating System Storage Database Network Management Applications Component Administrative Building Metropolitan Regional Recovery Point and Recovery Time are implicit to the Availability Matrix because there are products and capabilities to help with the analysis, and to establish and implement the practices necessary to assure that ECG064/1198