Compaq nc6000 Wireless Security - Page 8
Virtual Private Network vs. Reverse Proxy - memory
 |
View all Compaq nc6000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 8 highlights
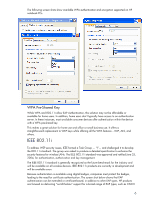
Virtual Private Network vs. Reverse Proxy Most people are using Virtual Private Network (commonly known as Tunnels) to connect to their corporate networks. Even consumer-grade wireless and wired routers have VPN and some Firewall and DMZ capabilities. An alternative to VPN that is rapidly gaining acceptance is the use of reverse proxy to obtain pervasive access. Reverse proxy passes http traffic back and forth across the firewall from the device to the back-end servers and web services - such as Microsoft Exchange, database servers, file servers and any web application. This is all done using http, https or http with AES, 3DES or other encryption to secure transmitted data. The following screen shots demonstrate how Microsoft Exchange Server can connect to the network without VPN, using HTTPS. This is an ideal solution for notebooks accessing wireless and mobile networks. Microsoft Exchange Server supports access to full PIM using Reverse Proxy when clicking "more settings." Nearly all applications - and many software solutions - use this method, including: device management, security solutions, PIM Synchronization, file sharing (such as Microsoft SharePoint) and database synchronization. This can include rich media and voice applications as well as Instant Messaging. Microsoft SQL 2005 and Microsoft VisualStudio 2005 will be tightly integrated and will support subsequent generations of the needed proxy code to enable synchronization of the database over http, where developers can add the needed security - such as Advanced Encryption Standard (AES), Secure Socket layer (SSL) or Data Encryption Standard (DES). AES is proving to be the optimal encryption for mobile devices, due to its low requirements of memory and CPU processing power. This has a huge impact on mobility in terms of battery life, time, price and total customer experience. 8