D-Link DES-3526 Product Manual - Page 200
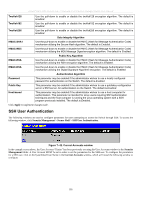
SSH User Authentication, Current Accounts window
 |
UPC - 790069265969
View all D-Link DES-3526 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 200 highlights
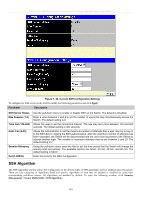
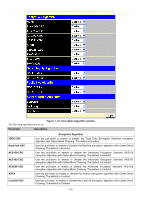
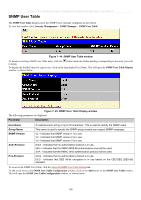
xStack® DES-3500 Series Layer 2 Stackable Fast Ethernet Managed Switch User Manual Twofish128 Use the pull-down to enable or disable the twofish128 encryption algorithm. The default is Enabled. Twofish192 Use the pull-down to enable or disable the twofish192 encryption algorithm. The default is Enabled. Twofish256 Use the pull-down to enable or disable the twofish256 encryption algorithm. The default is Enabled. Data Integrity Algorithm HMAC-SHA1 Use the pull-down to enable or disable the HMAC (Hash for Message Authentication Code) mechanism utilizing the Secure Hash algorithm. The default is Enabled. HMAC-MD5 Use the pull-down to enable or disable the HMAC (Hash for Message Authentication Code) mechanism utilizing the MD5 Message Digest encryption algorithm. The default is Enabled. Public Key Algorithm HMAC-RSA Use the pull-down to enable or disable the HMAC (Hash for Message Authentication Code) mechanism utilizing the RSA encryption algorithm. The default is Enabled. HMAC-DSA Use the pull-down to enable or disable the HMAC (Hash for Message Authentication Code) mechanism utilizing the Digital Signature Algorithm encryption. The default is Enabled. Authentication Algorithm Password This parameter may be enabled if the administrator wishes to use a locally configured password for authentication on the Switch. The default is Enabled. Public Key This parameter may be enabled if the administrator wishes to use a publickey configuration set on a SSH server, for authentication on the Switch. The default is Enabled. Host-based This parameter may be enabled if the administrator wishes to use a host computer for authentication. This parameter is intended for Linux users requiring SSH authentication techniques and the host computer is running the Linux operating system with a SSH program previously installed. The default is Enabled. Click Apply to implement changes made. SSH User Authentication The following windows are used to configure parameters for users attempting to access the Switch through SSH. To access the following window, click Security Management > Secure Shell > SSH User Authentication. Figure 7- 42. Current Accounts window In the example screen above, the User Account "Trinity" has been previously set using the User Accounts window in the Security Management folder. A User Account MUST be set in order to set the parameters for the SSH user. To configure the parameters for a SSH user, click on the hyperlinked User Name in the Current Accounts window, which will reveal the following window to configure. 185