Foxconn A74ML-K 3.0 English Manual. - Page 44
M Trusted Platform Module is a specification promoted by TCG. A Trusted Platform Mod
 |
View all Foxconn A74ML-K 3.0 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 44 highlights
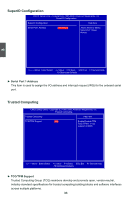
3 TPM (Trusted Platform Module) is a specification promoted by TCG. A Trusted Platform Module offers facilities for secure generation of cryptographic keys. The TPM Work Group is chartered to create the Trusted Platform Module (TPM) specification. The definition of the TPM architecture comes from the TC and the TPM Work Group defines the implementation of that architecture. Work group members should have a working knowledge of security in relation to the design and usage of cryptographic modules. Members should also have a working knowledge of cryptographic techniques including public-key cryptography, cryptographic algorithms and protocols. This item is used to enable/disable the function of TCG/TPM support. 37

3
37
TP
M (Trusted Platform Module) is a specification promoted by TCG. A Trusted Platform Mod
-
ule offers facilities for secure generation of cryptographic keys.
The TPM Work Group is chartered to create the Trusted Platform Module (TPM) specifica
-
tion. The definition of the TPM architecture comes from the TC and the TPM Work Group
defines the implementation of that architecture. Work group members should have a working
knowledge of security in relation to the design and usage of cryptographic modules. Members
should also have a working knowledge of cryptographic techniques including public-key cryp-
tography, cryptographic algorithms and protocols.
This item is used to enable/disable the function of TCG/TPM support.