HP 635n Practical IPsec Deployment for Printing and Imaging Devices - Page 35
IKE Authentication: Pre-shared Key
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 35 highlights
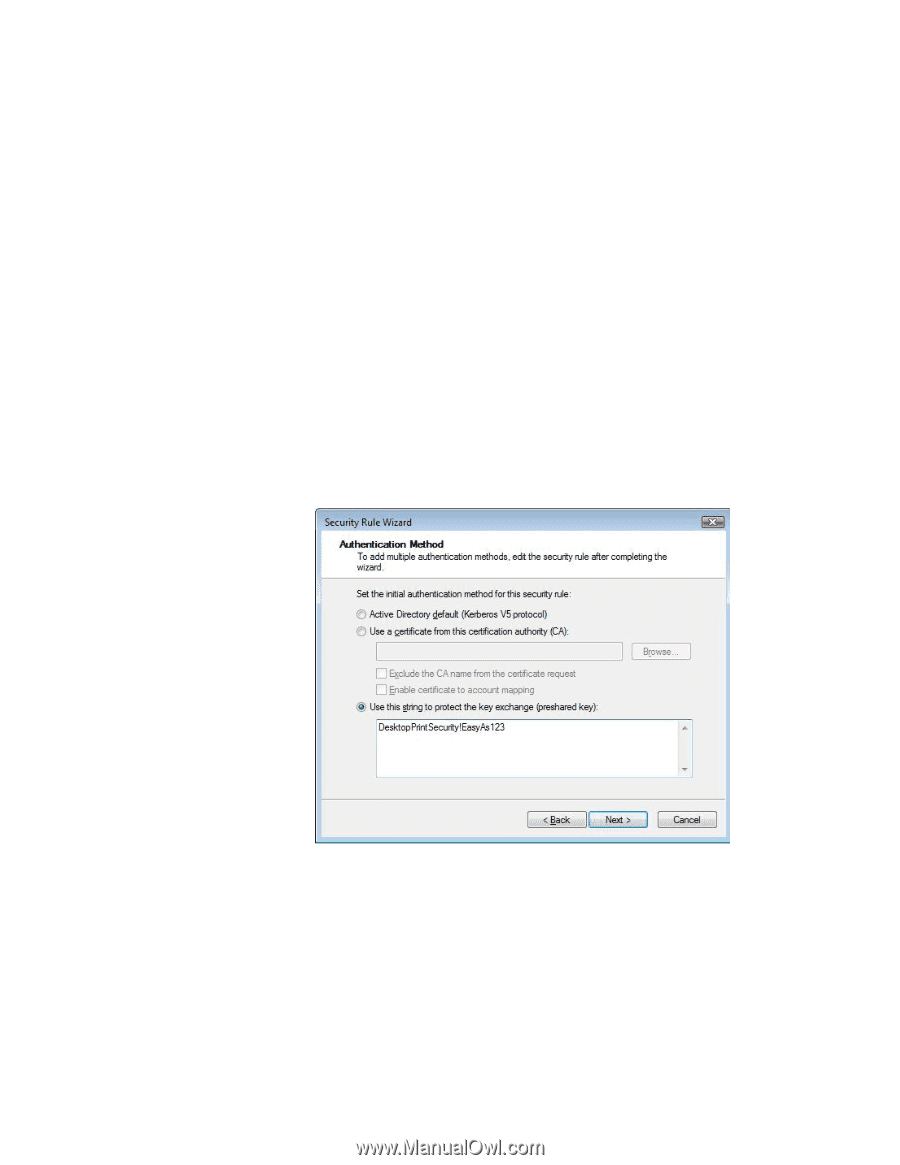
Diffie-Hellman doesn't really work this way, but in principle, this is how you would accomplish something similar. The point of the example is only to take a little mystery out of the process. Again, the different Diffie-Hellman groups, or DH groups, refer to different "strengths" of security. You can think of a bigger, more secure lock as being the same as a larger DH Group number. Well, at this point, IKE has selected the format of the SA and has secret keying material available to it. Now the only thing left to do is authenticate the computer system it is speaking to. Unfortunately, this can be pretty complex. There are three different authentication algorithms to verify that the computer system you are talking to is really the one you think you are talking to. They are Pre-Shared Key, Kerberos, and Certificates. IKE Authentication: Pre-shared Key The simplest way IKE can mutually authenticate two computer systems is through a shared secret passphrase, or as IKE refers to it as a Pre-shared Key. This value must be the same on both computer systems. The Authentication exchange uses the shared DH secret and hashes of the pass-phrase to determine if both computer systems know the pass-phrase without actually transmitting it over the network. To configure IKE Pre-Shared Key Authentication, you'll need to enter the exact same passphrase on both computer systems. Figure 27 shows a screen shot from Microsoft's IPsec Wizard. Figure 27 - Windows Authentication Method This next screen shot is from HP Jetdirect. Notice the pass phrases are the same and have to be the same for Pre-Shared Key authentication to work. 35