HP t5710 HP Sygate Security Agent User Guide - Page 41
Agent: Blocked or Allowed
 |
View all HP t5710 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 41 highlights
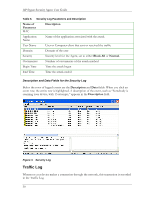
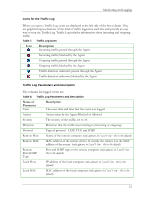
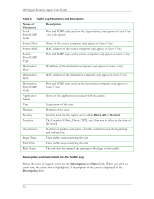
Monitoring and Logging Icons for the Traffic Log When you open a Traffic Log, icons are displayed at the left side of the first column. They are graphical representations of the kind of traffic logged on each line and provide an easy way to scan the Traffic Log. Traffic Log includes information about incoming and outgoing traffic. Table 7. Traffic Log Icons Icon Description Incoming traffic; passed through the Agent Incoming traffic; blocked by the Agent Outgoing traffic; passed through the Agent Outgoing traffic; blocked by the Agent Traffic direction unknown; passed through the Agent Traffic direction unknown; blocked by the Agent Traffic Log Parameters and Description The columns for logged events are: Table 8. Traffic Log Parameters and Description Name of Parameter Time Description The exact date and time that the event was logged Action Action taken by the Agent: Blocked or Allowed Severity The severity of the traffic, set to 10. Direction Direction that the traffic was traveling in (incoming or outgoing) Protocol Type of protocol - UDP, TCP, and ICMP Remote Host Name of the remote computer (only appears in Local View - this is the default) Remote MAC MAC address of the remote device. If outside the subnet, it is the MAC address of the router. (only appears in Local View - this is the default) Remote Port/ICMP Type Port and ICMP type on the remote computer (only appears in Local View this is the default) Local Host IP address of the local computer (only appears in Local View - this is the default) Local MAC MAC address of the local computer (only appears in Local View - this is the default) 31