Lenovo ThinkCentre M50 IDC white paper titled "The Coming of Age of Clien - Page 6
In a case involving far greater value, two Russian hackers were lured to the United
 |
View all Lenovo ThinkCentre M50 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 6 highlights
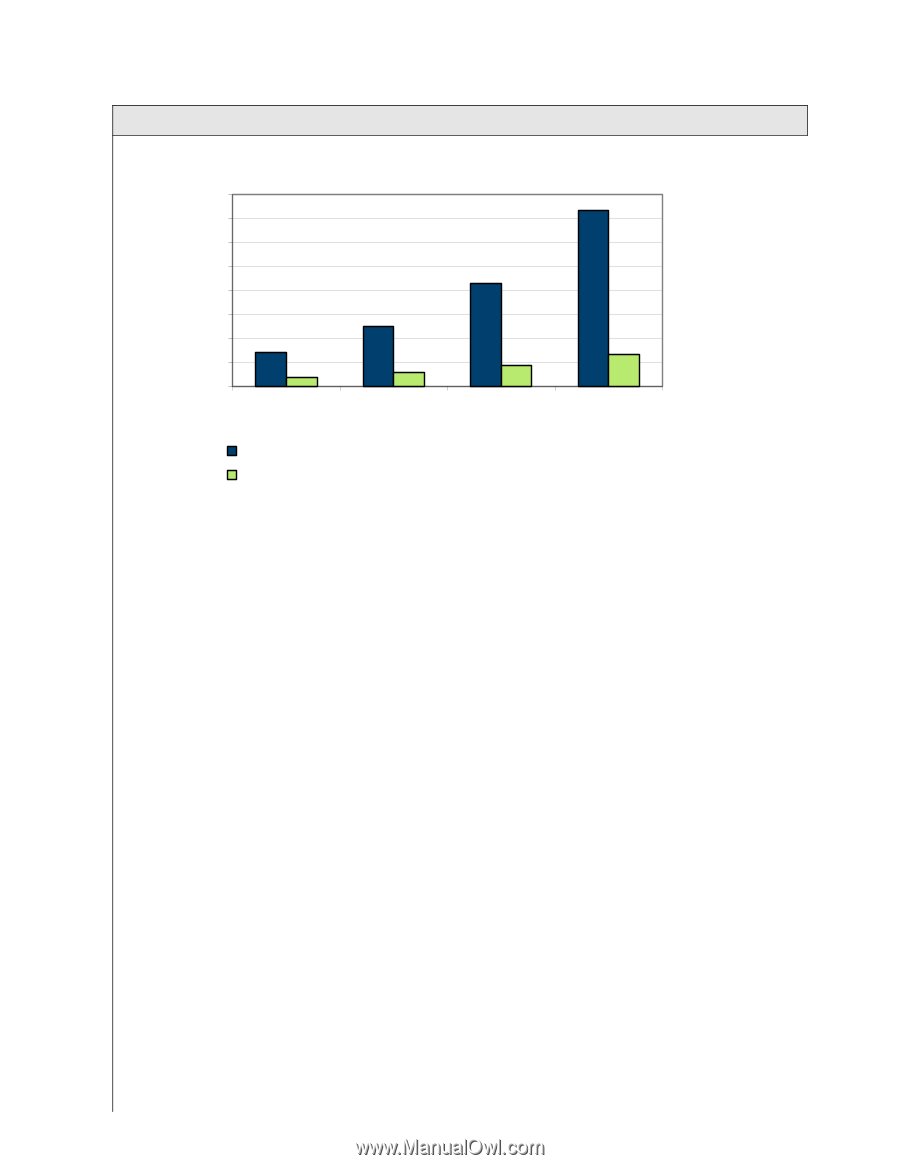
FIGURE 1 WORLDWIDE ECOMMERCE SPENDING BY TYPE, 2000-2003 ($B) 1,600 1,400 1,200 1,000 800 600 400 200 0 2000 2001 2002 B2B B2C Source: IDC's Internet Commerce Market Model version 8.1, February 2002 2003 Authorities in the United States recently cracked the case of a professional hacker based in the United Kingdom who had access to about 100 unclassified military networks during most of 2002. The case, which had been considered a high priority for a year, despite the unclassified nature of the networks, was a focus because of the skill of the hacker, who was finally snared. Although the exposed data was not particularly sensitive, the determination and talent of the hacker led authorities to believe that it would be only a matter of time before he uncovered something valuable. Among sites he was able to enter were the Pentagon Picatiny Arsenal in New Jersey, one of the Army's most delicate research facilities. And he was in the process of unfolding a multistage attack, the sign of a highly sophisticated hacker, at the time of his arrest. In a case involving far greater value, two Russian hackers were lured to the United States by federal agents on the pretext of a commercial interest. Once in Seattle, they were arrested. But until that moment, they had been engaged in an operation that had hacked into banks and ecommerce sites and extorted the operators for money with the promise of not revealing the hacks to the public. Sometimes the value of reputation damage is difficult to assess, but it may represent the entire value of the business. Another Russian hacker was monitored for years as he downloaded millions of pages of sensitive data from defense department computers, including one colonel's email inbox. Aiding and abetting the rise in attacks, the collective pool of hacking knowledge has risen. Hackers often trade schemes and software via Internet Relay Chat, better known by its initials, IRC, one of the least-regulated areas of the Internet and one that allows anonymous contact at the user's discretion. The packets flow to everywhere from everywhere. And although more policed areas of the Internet exist (e.g., AOL and other "communities" in cyberspace), the underlying structure still relies on realtime routing, and packet spoofing makes it possible for someone to conceal his whereabouts, particularly if he comes from a number of directions at once. 6 #3577 Aiding and abetting the rise in attacks, the collective pool of hacking knowledge has risen. Hackers often trade schemes and software via Internet Relay Chat, better known by its initials, IRC, one of the least-regulated areas of the Internet and one that allows anonymous contact at the user's discretion. ©2003 IDC