Dell PowerConnect W Clearpass 100 Software Palo Alto Networks User-ID Services - Page 11
Configuring User-ID Agent Definition, Device > User, Identification, Agent
 |
View all Dell PowerConnect W Clearpass 100 Software manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 11 highlights
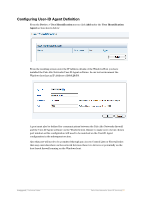
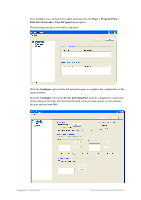
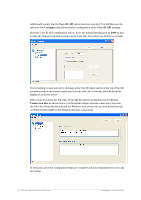
Configuring User-ID Agent Definition From the Device > User Identification screen click Add under the User Identification Agent section shown below: From the resulting screen enter the IP Address details of the Windows Host you have installed the Palo Alto Networks User-ID Agent software. In our test environment the Windows host has an IP Address of 10.0.20.53. A port must also be defined for communications between the Palo Alto Networks firewall and the User-ID Agent software on the Windows host. Ensure to make note of your chosen port number as this configuration will need to be matched on the User-ID Agent configuration in the subsequent section. Also this port will need to be permitted through any Access Control Lists or Firewall rules that may exist elsewhere on the network between these two devices or potentially on the host based firewall running on the Windows host. Amigopod |Technical Note Palo Alto Networks User-ID Services|11