Dell Powerconnect W-ClearPass Hardware Appliances W-ClearPass Policy Model - Page 3
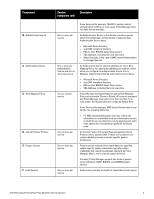
Component, Service, component ratio, Description, Static Host Lists
 |
View all Dell Powerconnect W-ClearPass Hardware Appliances manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 3 highlights
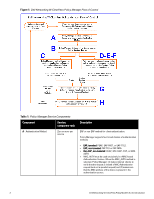
Component B - Authentication Source C - Authorization Source C - Role Mapping Policy D - Internal Posture Policies E - Posture Servers F - Audit Servers Service: component ratio Description Zero or more per service One or more per Authentication Source and zero or more per service Zero or one per service Zero or more per service Zero or more per service Zero or more per service Some Services (for example, TACACS+) contain internal authentication methods; in such cases, Policy Manager does not make this tab available. An Authentication Source is the identity repository against which Policy Manager verifies identity. It supports these Authentication Source types: l Microsoft Active Directory l and LDAP compliant directory l RSA or other RADIUS-based token servers l SQL database, including the local user store. l Static Host Lists, in the case of MAC-based Authentication of managed devices. An Authorization Source collects attributes for use in Role Mapping Rules. You specify the attributes you want to collect when you configure the authentication source. Policy Manager supports the following authorization source types: l Microsoft Active Directory l any LDAP compliant directory l RSA or other RADIUS-based token servers l SQL database, including the local user store. Policy Manager evaluates Requests against Role Mapping Policy rules to match Clients to Role(s). All rules are evaluated and Policy Manager may return more than one Role. If no rules match, the request takes the configured Default Role. Some Services (for example, MAC-based Authentication) may handle role mapping differently: l For MAC-based Authentication Services, where role information is not available from an authentication source, an Audit Server can determine role by applying post-audit rules against the client attributes gathered during the audit. An Internal Posture Policy tests Requests against internal Posture rules to assess health. Posture rule conditions can contain attributes present in vendor-specific posture dictionaries. Posture servers evaluate client health based on specified vendor-specific posture credentials, typically posture credentials that cannot be evaluated internally by Policy Manager (that is, not by internal posture policies). Currently, Policy Manager supports two forms of posture server interfaces: HCAP, RADIUS, and GAMEv2 posture servers. Audit servers evaluate the health of clients that do not have an Dell Networking W-ClearPass Policy Model 6.0 | An Introduction 3