Epson S60600 User Manual - Page 50
Configuration Workflow, Product Security Policies: An Overview
 |
View all Epson S60600 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 50 highlights
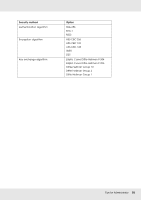
The product accepts only specific types of data from specific clients. In this example, security levels are set separately for each client type so that the product accepts all data from administrator clients (including product management and print data) but only print data from print clients and no data at all from other clients. Product Security Policies: An Overview O You can create one Default Policy and Group Policy 1-10. O If there is more than one policy, the product will check the policies in order from the top of the display ("Group Policy 1") and initiate a network connection when it finds a matching policy. O Because the product checks the policies in order from the top, more restrictive policies should precede the more general policies on which they are based. Configuration Workflow IPsec requires a client with secure access to the product and configured according to your purposes. Access Control requires that the product be configured according to your purposes. The configuration workflow is shown below. Note: If your network is already secure, we recommend that you connect the product to a computer on a different network before adjusting settings. There is potential for data theft if the product is connected to a secure network when settings are adjusted. If no other network is available, refer to the "Encrypting communications" below. 1. Connect the product and the computer that will be used to configure the product to the network. 2. Adjust Remote Manager settings. See the following page information on Remote Manager settings. 3. Transmit the settings to the printer.* 4. Adjust client computer security settings (not required for Access Control). 5. Connect the printer to a secure network. Tips for Administrator 50