HP 15-r022nr User Guide - Ubuntu - Page 47
and then lock the, security cable lock with the key.
 |
View all HP 15-r022nr manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 47 highlights
methods that should be employed as part of a complete security solution to help maximize theft protection. The security cable slot on your computer may look slightly different from the illustration in this section. 1. Loop the security cable lock around a secured object. 2. Insert the key (1) into the security cable lock (2). 3. Insert the security cable lock into the security cable slot on the computer (3), and then lock the security cable lock with the key. 4. Remove the key and keep it in a safe place. Using an optional security cable lock 39
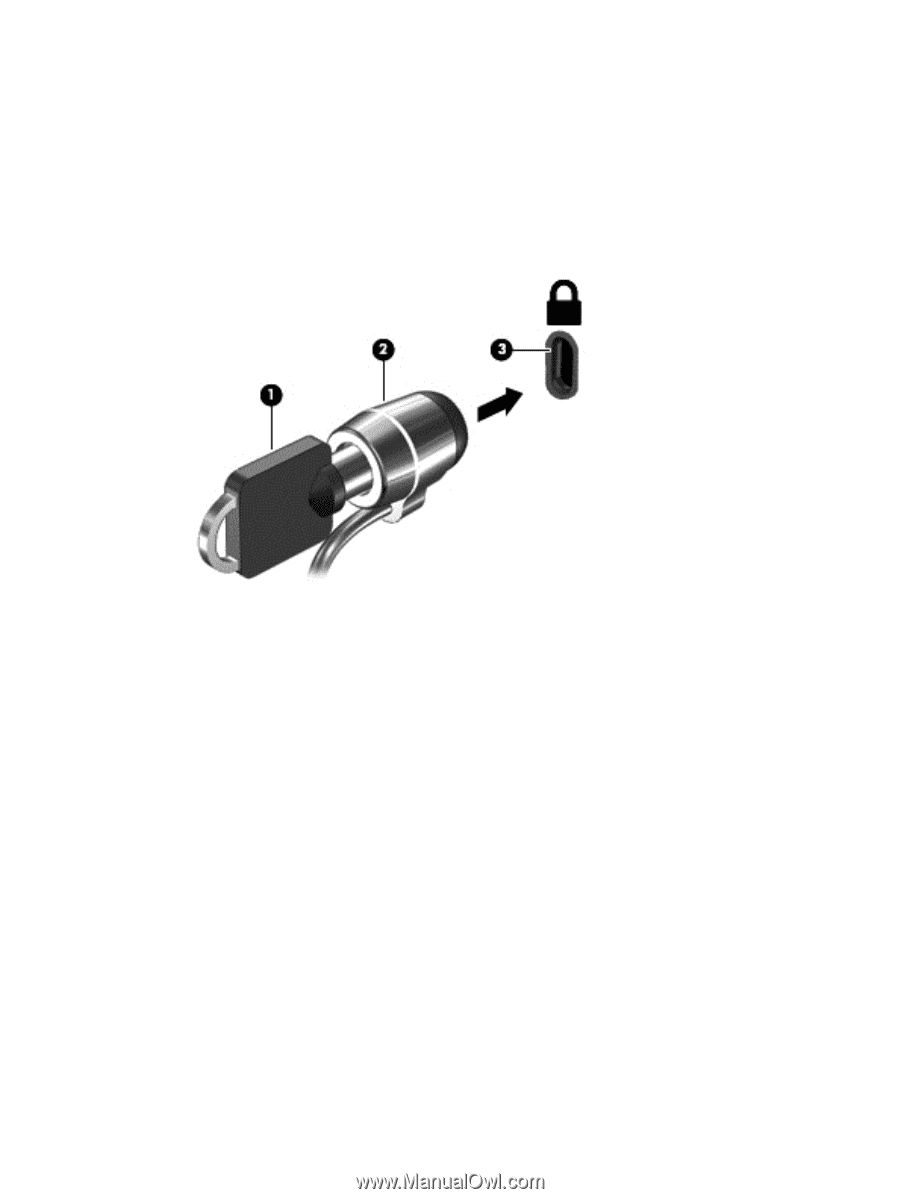
methods that should be employed as part of a complete security solution to help maximize theft
protection.
The security cable slot on your computer may look slightly different from the illustration in this section.
1.
Loop the security cable lock around a secured object.
2.
Insert the key
(1)
into the security cable lock
(2)
.
3.
Insert the security cable lock into the security cable slot on the computer
(3)
, and then lock the
security cable lock with the key.
4.
Remove the key and keep it in a safe place.
Using an optional security cable lock
39














