HP 5310m HP Business Notebook Password Localization Guidelines - Page 3
Overview of Design, Supported Keyboard Layouts in Preboot and Drive, Encryption - notebook case
 |
UPC - 884962601266
View all HP 5310m manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 3 highlights
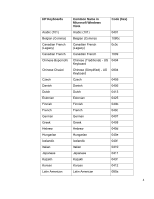
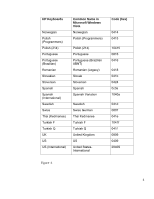
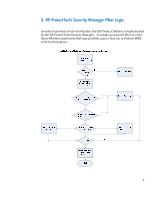
3. Overview of Design The goal of the HP ProtectTools implementation is to use password filters to reject passwords that might lock out a user at the Preboot BIOS level or Drive Encryption level. The ProtectTools Security Manager will be responsible to reject a user password at setup or password change time. A password can be acceptable for the Windows password, but if allowed may cause a lock out at Preboot BIOS or Drive Encryption level. These passwords will therefore be rejected by the HP ProtectTools password filter. The BIOS Preboot and Drive Encryption each preloads tables of key mapping from Scan Code to Unicode based on the supported keyboard layout. (see table Figure ‐1 below). When the user enters the password before OS starts, the BIOS or the Drive Encryption software will convert the key strokes to the correct Unicode based on key mapping tables and then compare the password with the one stored. The ProtectTools Security Manager will pass the keyboard layout information to BIOS Preboot and Drive Encryption. In addition, the BIOS Preboot and Drive Encryption may implement additional methods to assist password entering. E.g. In 2008 Business Notebook BIOS, a soft keyboard will be loaded to enter glyphs directly with the mouse instead of pressing a key on the keyboards if a user fails to type their password correctly. The Drive Encryption software allows the user to dynamically load the keyboard layouts. 4. Supported Keyboard Layouts in Preboot and Drive Encryption The Preboot BIOS and Drive Encryption support a subset of Windows' keyboard layouts due to space and other limitations. Below is a list (Figure 1) of supported keyboards in Preboot and Drive Encryption. In some cases, the common name for a particular keyboard layout differs in Windows Vista from the HP designation. In order to clarify, we provide both names. 3