HP 8730w HP Business Notebook Password Localization Guidelines - Page 7
How Preboot BIOS Implements the Password Filter And, Handles Dead Keys
 |
UPC - 884962212455
View all HP 8730w manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 7 highlights
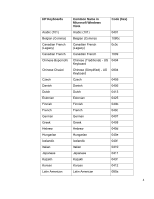
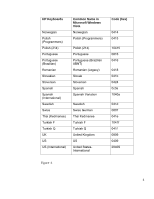
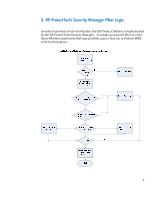
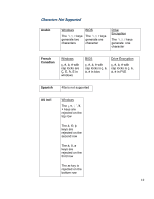
6. How Preboot BIOS Implements the Password Filter And Handles Dead Keys The HP BIOS implements a second level password filter to further prevent the lock‐out situation. HP BIOS Preboot and HP Drive Encryption contain the keyboard mappings for all the supported keyboards listed above. When a user is setting up Preboot Security with the BIOS Preboot or Drive Encryption levels enabled, or when a user changes his/her password, the BIOS Preboot and Drive Encryption receives the Unicode password from the OS. The BIOS is responsible to guarantee that the keyboard being associated with that user is able to type the password. Otherwise, the BIOS will reject the password. However, there still may be an instance where the user changes the keyboard in Windows without the BIOS's knowledge or when the user is not aware of the keyboard layout currently in use. To compensate for the situation where the user may not be able to physically type their password due to these two situations, the BIOS will automatically provide the user the ability to "click" out her/his password after failing with the physical keyboard. This is done by showing every character on the screen that could be typed with the keyboard currently associated with the user, each of them as buttons and which can be clicked with the mouse to form the password. This method provides a way for the user to enter the password without the physical keyboard. (Please note: When using the "On‐Screen Keyboard" in the BIOS, there are many characters shown and some characters may look very similar to others on some keyboards. If experiencing trouble using this feature, so please look at all of the characters before clicking out your password to ensure you are entering the correct characters.) In the BIOS, the use of Dead Keys has also been added to try to provide the user with as much keyboard functionality as possible. If for some reason a certain character is produced on the OS level that cannot be typed in the BIOS, this will cause the password change to be rejected. Unless rejected, the user should feel safe and confident in using Dead Keys for passwords associated with the Preboot Security feature. This ability of the Preboot Security hinges on its ability to ensure that the Windows password can always be entered in the Preboot BIOS and Drive Encryption, and therefore all characters that require special typing methods that are not common to all keyboards, such as the use of the Kana key or the use of IME function of Windows, will result in the password change being rejected from the BIOS, as the BIOS does not contain these advanced typing features. 7