HP J2383B HP Jetdirect Print Servers - Philosophy of Security - Page 18
Luckily, the Internet Explorer 7
 |
View all HP J2383B manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 18 highlights
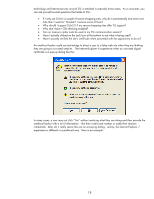
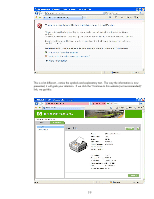
technology and Internet security around SSL is attacked in precisely those areas. As a consumer, you can ask yourself several questions that relate to SSL: • If I only use SSL for a couple of secure shopping sites, why do I automatically trust more root CAs than I need to? Shouldn't I remove some of them? • Why should I support SSLv2.0 if my secure shopping sites offer TLS support? • Why don't have I CRL checking enabled? • Can an insecure cipher suite be used in my SSL communication session? • Have I actually clicked on the Lock Icon at the bottom to see what is being used? • Have I actually verified the site's certificate when presented with the opportunity to do so? An unethical hacker could use technology to direct a user to a false web site when they are thinking they are going to a trusted website. The Internet Explorer 6 experience when an untrusted digital certificate is a pop-up dialog like this: In many cases, a user may just click "Yes" without realizing what they are doing and then provide the unethical hacker with a lot of information - like their credit card number or sadly their domain credentials. After all, it really seems like just an annoying dialog. Luckily, the Internet Explorer 7 experience is different in a profound way. Here is an example: 18