HP nx9030 WLAN solutions for HP enterprise notebooks and Tablet PCs - Page 4
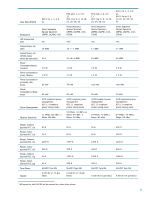
Manageability - specifications
 |
View all HP nx9030 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 4 highlights
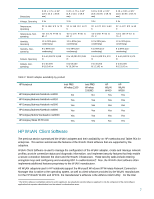
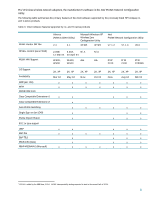
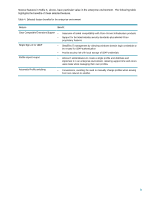
Defined as part of the IEEE 802.11 family of WLAN specifications, WEP security was intended to make wireless networks as secure as wired LANs. However, with the symmetrical RC4 stream cipher2 and static 64- or 128-bit key, WEP security was insufficient for some environments. WPA was introduced in mid 2003 as an immediately-available, software-upgradable enhancement for WEP. WPA enhanced WEP encryption through the addition of Temporal Key Integrity Protocol (TKIP), providing perpacket key mixing, Message Integrity Check (MIC), extended initialization vector (IV) with sequencing rules, and a re-keying mechanism. WPA is significantly more secure than WEP3, and has received acceptance from most enterprise IT managers. AES is a block cipher using the Rijndael encryption algorithm on 128-bit (or 192- or 256-bit) blocks of data; block lengths and key lengths are variable. (Block ciphers are typically more complex than stream ciphers and thus harder to crack. The strength of AES security is validated by its adoption by the U.S. government and military.) AES is a key component of the IEEE 802.11i specification, the most recent WLAN security standard that was ratified in June 2004 by IEEE Task Group i (TGi) working group members. HP's current WLANs include AES support, and will support 802.11i and the corresponding Wi-Fi interoperability test WPA2 through a future software upgrades. Manageability For large WLAN deployments, the effort required to implement and maintain WLAN security measures can be significant. Manageability features of HP WLAN solutions include: Restricted user rights User rights to certain settings may be restricted to prevent modifying WLAN profiles (for example, security keys), and in some cases from creating new profiles. Easy distribution of encryption keys and user profiles The management and distribution of encryption keys and user profiles can be cumbersome and potentially insecure. Appropriate WLAN management solutions-such as 802.1x and the ability to import and export WLAN profiles-can be used to distribute keys and profiles, minimizing the burden on IT staff. User credential management HP addresses the need for the security and simplified management of user credentials by allowing Windows® Domain credentials to be re-used for LEAP authentication. Security can also be further enhanced by the HP ProtectTools Security Manager-a single client console application that unifies security capabilities of HP client PCs under a common architecture and single user interface. Today a range of features is being delivered that builds on underlying hardware security building block,s such as embedded security chips designed to the Trusted Computing Group (TCG) standard and Smart Card technology. Collectively, these features are addressing business customer needs for better protection against unauthorized PC access, as well as stronger protection for sensitive data stored locally or accessed over a network. Managed product lifecycles and software upgrades Stable product configurations over a long purchase period ease IT management by minimizing technology transitions. WLAN driver and client software that are compatible across multiple notebooks and WLAN adapters, and are backwards compatible with previous revisions, simplify maintenance of the WLAN installed base. 2 For more information, visit www.rsasecurity.oom 3 Wi-Fi Protected Access Whitepaper, available at www.wi-fi.org 4