Ricoh 2020D Features Guide - Page 12
US Department of Defense Common Access Card (CAC) Authentication
 |
View all Ricoh 2020D manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 12 highlights
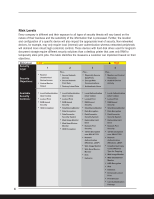
Ricoh Aficio Common Security Features Guide In addition, when using Windows Authentication or the internal User Code function, it is possible to restrict access to specific features, such as whether or not to allow individual users and/or groups to print in color. US Department of Defense Common Access Card (CAC) Authentication The Common Access Card (CAC) is a US DoD specialized ID card-based authentication system design to make Ricoh MFP's compliant with the Homeland Security Presidential Directive -12 (HSPD-12). This Directive requires that all federal employees and contractors enhance security efficiently by reducing identity fraud through increased protection of personal privacy. The only customers for Ricoh's CAC Authentication Solution is the U.S. Department of Defense (DoD) [US Army, Navy Air Force, Marines, Coast Guard and affiliated agencies]. IP (Internet Protocol) Address Filtering In a LAN, an IP Address is each networked computer's unique hardware number. Just like your street address with a house or apartment number, these addresses help route e-mails and attachments, forward faxes to the proper recipient, and send print data to networked output devices from originating PCs. The ability of Ricoh devices to block/restrict a particular end-user or set of end-users based on an IP address improves the management of PCs and users, helps to balance output volumes among multiple devices, and enhances network security by limiting access to files stored in devices. Job Logs / Access Logs A complete listing of every job executed by the device is stored in memory. This list may be viewed via Web SmartDeviceMonitor to track and trace device usage by job and/or user. When used in conjunction with external user authentication modes, it will be possible to determine which specific users may be abusing a device, or whom and which device was used to send an unauthorized transmission to trace the source of leaks. 9