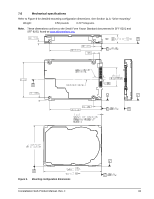
Seagate ST91000642SS Constellation SAS Product Manual - Page 43
About self-encrypting drives
 |
View all Seagate ST91000642SS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 43 highlights
9.0 About self-encrypting drives Self-encrypting drives (SEDs) offer encryption and security services for the protection of stored data, commonly known as "protection of data at rest." These drives are compliant with the Trusted Computing Group (TCG) Enterprise Storage Specifications as detailed in Section 3.2. The Trusted Computing Group (TCG) is an organization sponsored and operated by companies in the computer, storage and digital communications industry. Seagate's SED models comply with the standards published by the TCG. To use the security features in the drive, the host must be capable of constructing and issuing the following two SCSI commands: • Security Protocol Out • Security Protocol In These commands are used to convey the TCG protocol to and from the drive in their command payloads. 9.1 Data encryption Encrypting drives use one inline encryption engine for each port, employing AES-128 data encryption in Cipher Block Chaining (CBC) mode to encrypt all data prior to being written on the media and to decrypt all data as it is read from the media. The encryption engines are always in operation, cannot be disabled, and do not detract in any way from the performance of the drive. The 32-byte Data Encryption Key (DEK) is a random number which is generated by the drive, never leaves the drive, and is inaccessible to the host system. The DEK is itself encrypted when it is stored on the media and when it is in volatile temporary storage (DRAM) external to the encryption engine. A unique data encryption key is used for each of the drive's possible16 data bands (see Section 9.5). 9.2 Controlled access The drive has two security partitions (SPs) called the "Admin SP" and the "Locking SP." These act as gatekeepers to the drive security services. Security-related commands will not be accepted unless they also supply the correct credentials to prove the requester is authorized to perform the command. 9.2.1 Admin SP The Admin SP allows the drive's owner to enable or disable firmware download operations (see Section 9.4). Access to the Admin SP is available using the SID (Secure ID) password or the MSID (Makers Secure ID) password. Constellation SAS Product Manual, Rev. F 35