Compaq Evo n800c Wireless Security - Page 4
Security and the Pipe - support
 |
View all Compaq Evo n800c manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 4 highlights
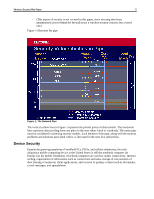
Wireless Security White Paper 4 Essential Elements of Security The essential elements of security as it applies to wireless networks are: • Privacy - assuring that only people who have permission to do so can view information and transactions. Privacy is preserved through a process that authorizes identified persons to see protected information and engage in transactions. Encryption is an important tool for preserving privacy. • Authentication - the process of verifying that the parties to an electronic transaction, as well as persons seeking access to digital information, are who they say they are. Authentication verifies identity and is supported by digital signatures. • Integrity - a process by which a security system seeks to preserve stored information and information that circulates in messages. Assuring that such information remains intact and unchanged (except by authorized parties) preserves its integrity. • Non-repudiation -- a process that proves an entity took a course of action, and only that entity could have taken the course of action. This quality makes electronic transactions legally binding. Non-repudiation is supported by digital signatures and trusted timestamps. • System Management -- all security technology must be managed. This means setting it up to be easy to use, while making sure it cannot be abused or used to hide criminal activity. These essential elements should be the result of any combination of security implementations from the device across the "pipe" to the corporate firewall and servers. The next section describes aspects of securing the "pipe", the security issues that may arise with wireless networks at critical junctures along the pipe, and measures that can be taken to address those issues. Security and the Pipe A pipe is a conduit through which something flows. A wireless mobile business solution should include an end-to end security model for enabling secure data access by creating a secure pipe from the mobile user's access device (the client) across various networks (air, broadband, dial-up) to the point where access is gained to the corporate network. From here the pipe leads through the corporate firewall to corporate applications. The end-to-end security model should also provide management mechanisms for performance and security. Key elements of the pipe are the following: 1. Security at the mobile access device level or client (Device Security) 2. Security in wireless connectivity technologies (Connectivity Technologies) - WLAN, WPAN, WWAN, broadband, dial-up, RAS 3. Security at the point of access to the wired transmission path (Access Point) - WLAN hubs, telecommunications companies 4. Security at the corporate firewall and servers (Corporate Access) 5. Security of the corporate data inside the firewall (Corporate Data)