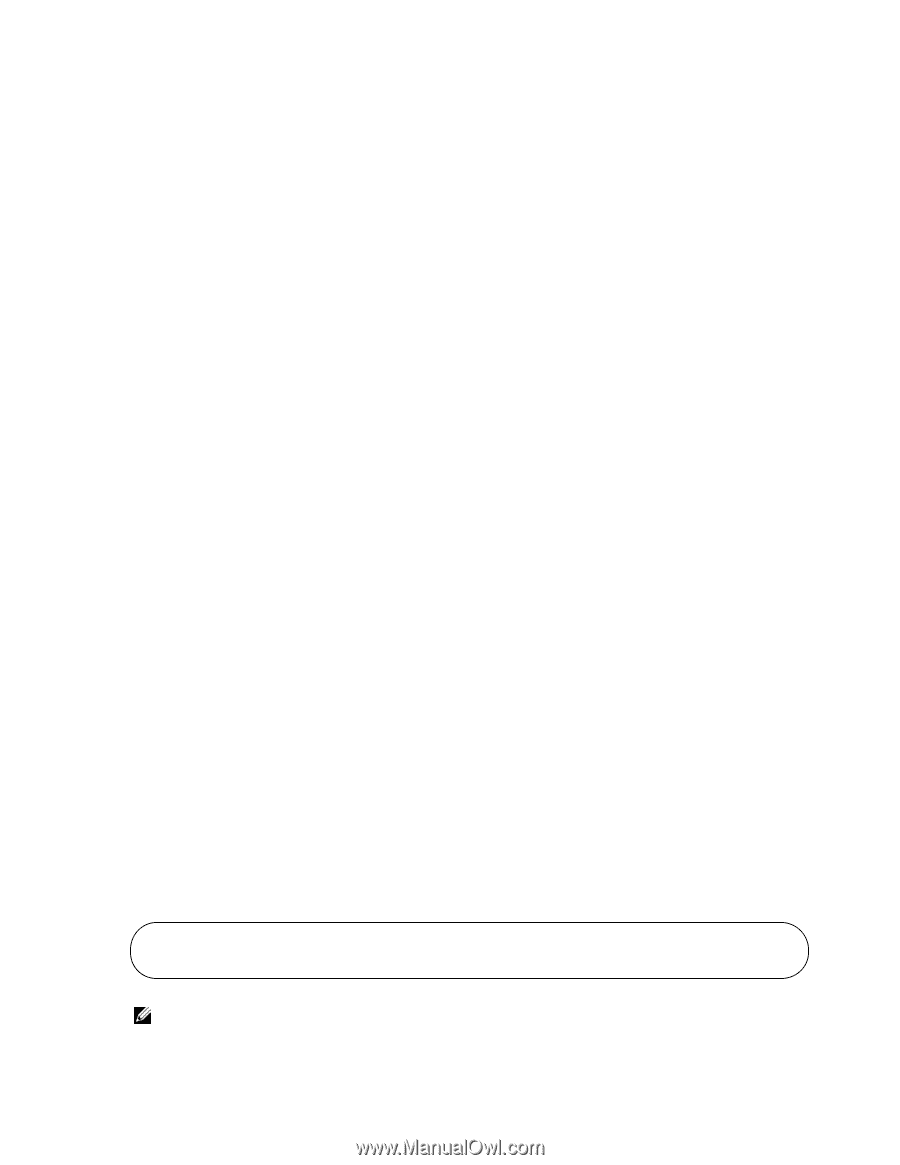Dell Force10 S2410-01-10GE-24P SFTOS Configuration Guide - Page 200
IP ACL Commands, Standard IP ACLs, Extended IP ACLs
 |
View all Dell Force10 S2410-01-10GE-24P manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 200 highlights
www.dell.com | support.dell.com IP ACL Commands IP ACLs ensure that only authorized users have access to specific resources and block any unwarranted attempts to reach network resources. The following rules apply to IP ACLs: • SFTOS does not support IP ACL configuration for IP packet fragments. • The maximum number of ACLs you can create is 100, regardless of type. • The maximum number of rules per IP ACL is hardware dependent. • On S-Series systems, if you configure a MAC ACL (see MAC ACL Commands on page 198) on an interface, you cannot configure an IP ACL on the same interface. • Wildcard masking for ACLs operates differently from a subnet mask. A wildcard mask is in essence the inverse of a subnet mask. With a subnet mask, the mask has ones (1's) in the bit positions that are used for the network address, and has zeros (0's) for the bit positions that are not used. In contrast, a wildcard mask has (0's) in a bit position that must be checked. A '1' in a bit position of the ACL mask indicates the corresponding bit can be ignored. The access-list command creates an IP ACL that is identified by the parameter ACLnumber, rendered as 1-99 for a Standard IP ACL or 100-199 for an Extended IP ACL, as discussed next. Standard IP ACLs A Standard IP ACL uses a list number in the range of 1-99, matches source IP address, then takes the action of assigning the packet to a queue and/or redirecting the packet to a destination port. access-list 1-99 {deny | permit} {every | srcip srcmask} [log] [assign-queue queue-id] [{mirror | redirect} unit/slot/port] Extended IP ACLs An extended IP ACL uses a list number in the range of 100-199, matches protocol type, then matches source and/or destination ip address/port, additionally matches ip-precedence, tos, dscp, then takes the action of assigning the packet to a queue and/or redirecting the packet to a destination port. The command has the general form: access-list 100-199 {deny | permit} {every | icmp | igmp | ip | tcp | udp | protocol_number} {any | srcip srcmask} {any | eq {portkey | 0-65535}{any | dstip dstmask} [eq {portkey | 0-65535}] [precedence precedence | tos tos tosmask | dscp dscp] [log] [assign-queue queue-id] [{mirror | redirect} unit/slot/port] Figure 13-159. Using the access-list Command for an Extended IP ACL Rule Force10 (Config)#access-list 100 permit ip any eq 80 any assign-queue 2 redirect 1/0/40 Force10 (Config)# Note: In both versions of the access-list command, above, srcmask is an inverse mask. Note: You cannot edit a rule once it is created, you must delete the list and create one as desired. 200 | Access Control