HP T5700 HP Sygate Security Agent User Guide - Page 47
Saving Logs, Stopping an Active Response, Trace route, WhoIs>>, Detail information, Ctrl+C
 |
View all HP T5700 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 47 highlights
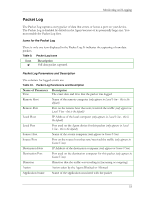
Monitoring and Logging The Trace route field provides details, such as IP address, on each hop made by the data packet that was logged by the Agent. A hop is a transition point, usually a router, that a packet of information travels through at as it makes its way from one computer to another on a public network, such as the Internet. 4. To view detailed information on each hop, click the WhoIs>> button. A drop panel displays detailed information about the owner of the IP address from which the traffic event originated. Note that the information displayed does not guarantee that you have discovered who the hacker actually is. The final hop's IP address lists the owner of the router that the hackers connected through, and not necessarily the hackers themselves. 5. Click either Whois