HP Tc4200 HP ProtectTools: Authentication technologies and suitability to task - Page 3
Password authentication - operating system
 |
View all HP Tc4200 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 3 highlights
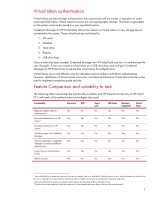
Credential Manager for HP ProtectTools currently supports the following authentication technologies: Credential Password Trusted Platform Module (TPM) Smart card USB token Biometric Fingerprint Virtual token Description Requires the user to create a unique passphrase and use it for identification. A cryptographic security chip embedded in a client PC or other computing device that is able to protect credentials and cryptographic functions. A type of token that, used properly, provides strong user authentication where credentials and cryptographic operations are contained within the smart card chip. An external device connected to a USB or other port interface that uses an integrated security chip to protect credentials and sensitive cryptographic functions. Uses fingerprint matching technology to provide a more convenient alternative to passwords and tokens. Enables virtually any storage device to be used as an authentication credential, including USB flash drives, where a protected file stored on the device is required to authenticate. Password authentication Passwords are the most common form of user authentication currently in use. Passwords require little or no unique infrastructure to implement and are useful for deterring casual access. Passwords can also be cost effective and a good level of protection can be achieved by utilizing simple and established policies for the creation of strong passwords. Many users however do not create strong1 passwords, and instead use passwords that have a personal significance. While these passwords are easy to remember for the user, they can also potentially be guessed by someone determined to break into the system. Stronger policies can be enforced by an IT administrator. However, doing so can sacrifice usability, and cause users to employ unsafe practices that can compromise security such as writing down the password in a location where it can be seen by someone else. Even strong and carefully protected passwords can be compromised via contact with keyboard monitoring viruses or other forms of commonly used network attacks. To compound the problem, a compromised password can go undetected, which means timely steps cannot be taken to protect the network. This can expose a corporate network to unauthorized access over longer duration and result in greater damage over time. 1 Weak passwords are referred to as such because they are easy to guess. Weak passwords may consist of sequential numbers or letters, or be derived from a user's personal information such as spouse name or birthday. Strong passwords on the other hand follow a set of criteria designed to ensure that the password is difficult to guess. These criteria allow users to create passwords that are not derived from personal information, and are therefore difficult to guess for the unauthorized user, yet easy to remember for the authorized user. 3