Konica Minolta bizhub C280 Product Guide - Page 177
Network Security
 |
View all Konica Minolta bizhub C280 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 177 highlights
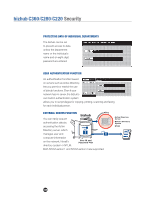
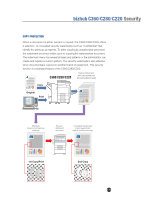
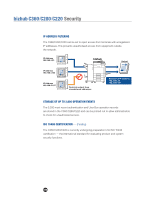
bizhub C360/C280/C220 Security Network Security NETWORK AUTHENTICATION The Network Authentication function uses the Active Directory service, Novell's directory system or NTLM to permit or restrict access to the C360/C280/C220 through the network. NTLM version 1 and NLM version 2 are supported. SMTP AUTHENTICATION FOR EMAIL DISTRIBUTION The C360/C280/C220 supports SMTP Authentication when using Scan-to-Email. This function strengthens protection against spamming and computer viruses by letting you use an Email server equipped with an authentication function. To prevent improper use of the Email Server when sending mail, users must enter both an ID number and a password. SCAN ENCRYPTION SSL Encryption protects scanned data over a TCP socket. PDF files scanned at the MFP can be encrypted. Scanned files are encoded in such a way that only those with the Key (password) can decode the message. With an "embedded" scan encryption function, users are able to perform the encryption directly at the desktop. There is no need to scan it, file it electronically, retrieve it using an application such as Adobe Acrobat, apply the encryption and then electronically distribute the encrypted file. All these steps can be eliminated and yet you are still allowed the encryption level and permissions available to you in Adobe Acrobat. The user does not need to sacrifice any type of functionality or security by performing the scan encryption at the device. 173