Cisco SLM2024 Administration Guide - Page 42
Port Security, Setting Timer - user manual
 |
UPC - 745883580002
View all Cisco SLM2024 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 42 highlights
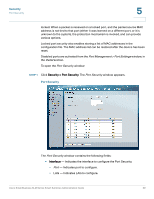
Security Port Security 5 The Setting Timer button opens the Setting Timer window to configure interface timers for 802.1x functionality. The Setting Timer window contains the following fields: • Port - Indicates the interface. • Reauthentication Period - Specifies the number of seconds in which the selected port is reauthenticated (Range: 300-4294967295). The field default is 3600 seconds. • Quiet Period - Specifies the number of seconds that the switch remains in the quiet state following a failed authentication exchange (Range: 0-65535). • Resending EAP - Specifies the number of seconds that the switch waits for a response to an EAP - request / identity frame, from the supplicant (client), before resending the request. • Max EAP Requests - The total amount of EAP requests sent. If a response is not received after the defined period, the authentication process is restarted. The field default is 2 retries. • Supplicant Timeout - Displays the number of seconds that lapses before EAP requests are resent to the supplicant (Range: 1-65535). The field default is 30 seconds. • Server Timeout - Specifies the number of seconds that lapses before the switch resends a request to the authentication server (Range: 1-65535). The field default is 30 seconds. • The table displays the basic information per port. STEP 2 Define the relevant fields. STEP 3 Click Save Settings. The settings are modified, and the device is updated. Port Security Network security can be increased by limiting access on a specific port only to users with specific MAC addresses. The MAC addresses can be dynamically learned or statically configured. Locked port security monitors both received and learned packets that are received on specific ports. Access to the locked port is limited to users with specific MAC addresses. These addresses are either manually defined on the port, or learned on that port up to the point when it is Cisco Small Business SLM Series Smart Switches Administration Guide 38