D-Link DSR-150 DSR-150 User Manual - Page 104
Web Content Filtering
 |
View all D-Link DSR-150 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 104 highlights
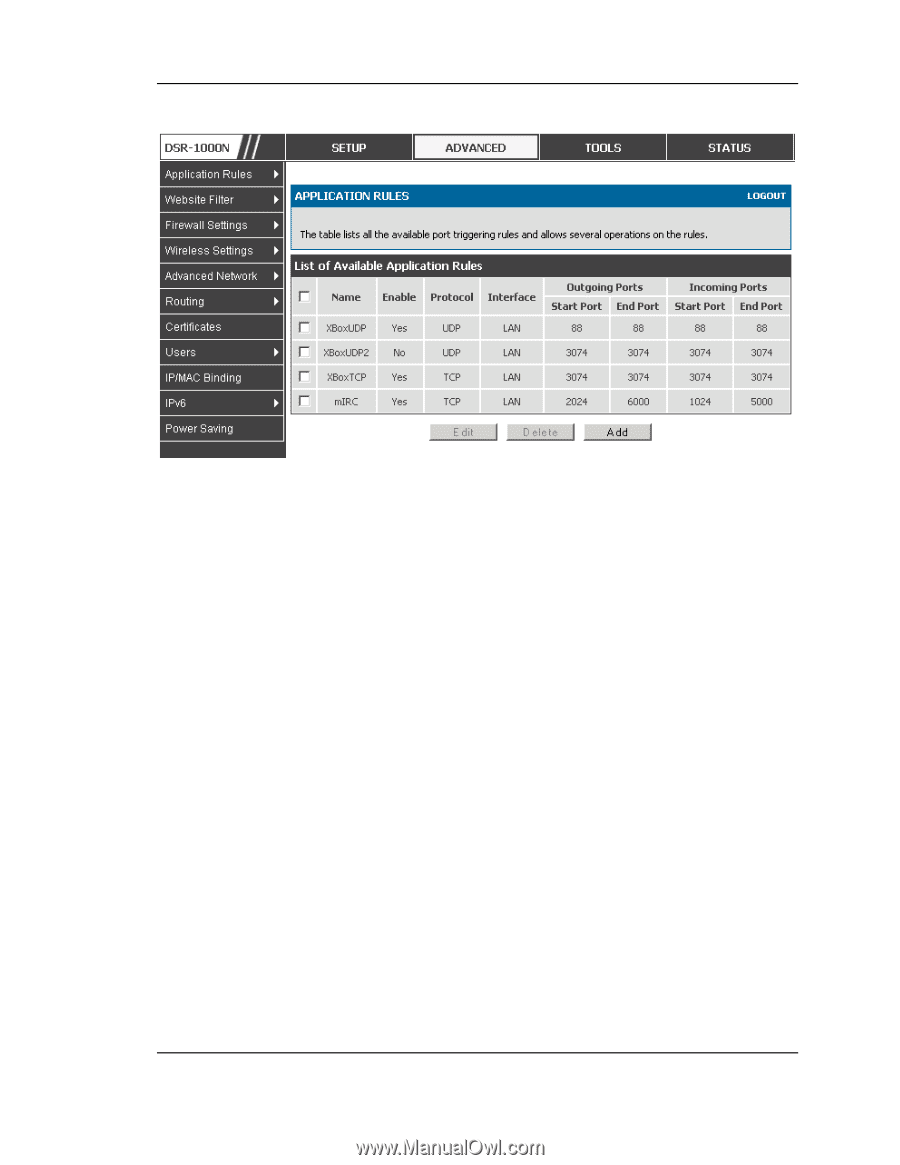
Unified Services Router User Manual Figure 63: Lis t of Available Applicat io n Rule s s howing 4 unique rule s Th e ap p licat io n ru le s t atus p age will lis t an y act iv e ru les , i.e. in co min g p o rt s t h at are being triggered bas ed on outbound reques ts from a defined outgoing port. 5.9 Web Content Filtering Th e g at eway o ffers s ome s t andard web filt erin g o p t io n s t o allo w t h e ad min t o eas ily creat e in t ern et access p o licies b etween t h e s ecu re LA N an d in s ecure W AN. In s tead o f creat in g p o licies b ased o n t he t y pe o f t raffic (as is t h e case wh en u s ing firewall ru les), web b as ed co n t en t it s elf can b e u s ed t o d et ermin e if t raffic is allo wed o r d ro p p ed . 5.9.1 Content Filtering Advanced > Website Filter > Content Filtering Co n t en t filt erin g mu s t b e en abled t o co n figu re an d u se t h e s ubsequent featu res (lis t o f Tru s t ed Do main s , filt erin g o n Blo cked Key wo rds , et c.). Pro xy s erv ers , wh ich can b e u s ed t o circu mv en t cert ain firewall ru les an d t h u s a p o t en t ial s ecu rit y g ap , can b e b lo cked fo r all LA N d ev ice s . Jav a ap p let s can b e p rev en t ed fro m b ein g d o wn lo ad ed fro m in t ern et s it es , an d s imilarly t h e g at eway can p rev en t A ct iv eX co n t ro ls fro m b ein g d o wn lo aded v ia In t ernet Exp lo rer. Fo r ad d ed s ecu rit y co o kies , wh ich t y p ically co n t ain s es s io n in fo rmat io n , can b e b lo cked as well fo r all d ev ices o n t h e p riv at e n e t wo rk. 102