Dell PowerConnect W-Series FIPS Dell PowerConnect W-AP134/5 Security Policy - Page 27
Wireless Client Services, 2.4 Unauthenticated Services
 |
View all Dell PowerConnect W-Series FIPS manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 27 highlights
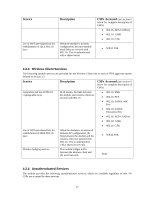
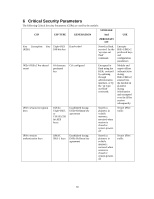
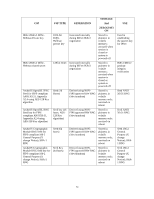
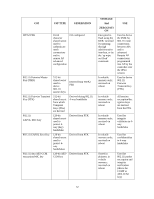
Service Use of WPA pre-shared key for establishment of IEEE 802.11i keys Description When the module is in mesh configuration, the inter-module mesh links are secured with 802.11i. This is authenticated with a shared secret CSPs Accessed (see section 6 below for complete description of CSPs) 802.11i AES-CCM key 802.11i GMK 802.11i GTK WPA2 PSK 4.2.3 Wireless Client Services The following module services are provided for the Wireless Client role in each of FIPS approved modes defined in section 3.3. Service Description CSPs Accessed (see section 6 below for complete description of CSPs) Generation and use of 802.11i cryptographic keys In all modes, the links between the module and wireless client are secured with 802.11i. 802.11i PMK 802.11i PTK 802.11i EAPOL MIC Key 802.11i EAPOL Encryption Key 802.11i AES-CCM key 802.11i GMK 802.11i GTK Use of WPA pre-shared key for establishment of IEEE 802.11i keys When the module is in advanced Remote AP configuration, the links between the module and the wireless client are secured with 802.11i. This is authenticated with a shared secret only. WPA2 PSK Wireless bridging services The module bridges traffic between the wireless client and the wired network. None 4.2.4 Unauthenticated Services The module provides the following unauthenticated services, which are available regardless of role. No CSPs are accessed by these services. 27