Dell PowerEdge M820 Dell PowerConnect M6220/M6348/M8024 Switches Configuration - Page 113
RADIUS, RADIUS Configuration Examples
 |
View all Dell PowerEdge M820 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 113 highlights
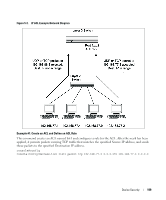
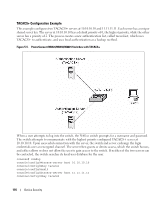
MAC ACL Name: mac1 Rule Number: 1 Action deny Destination MAC Address 00:11:22:33:44:55 Destination MAC Mask 00:00:00:00:FF:FF Log TRUE RADIUS Making use of a single database of accessible information-as in an Authentication Server-can greatly simplify the authentication and management of users in a large network. One such type of Authentication Server supports the Remote Authentication Dial In User Service (RADIUS) protocol as defined by RFC 2865. For authenticating users prior to access, the RADIUS standard has become the protocol of choice by administrators of large accessible networks. To accomplish the authentication in a secure manner, the RADIUS client and RADIUS server must both be configured with the same shared password or "secret". This "secret" is used to generate one-way encrypted authenticators that are present in all RADIUS packets. The "secret" is never transmitted over the network. RADIUS conforms to a secure communications client/server model using UDP as a transport protocol. It is extremely flexible, supporting a variety of methods to authenticate and statistically track users. RADIUS is also extensible, allowing for new methods of authentication to be added without disrupting existing functionality. As a user attempts to connect to a functioning RADIUS supported network, a device referred to as the Network Access Server (NAS) or switch/router first detects the contact. The NAS or user-login interface then prompts the user for a name and password. The NAS encrypts the supplied information and a RADIUS client transports the request to a pre-configured RADIUS server. The server can authenticate the user itself, or make use of a back-end device to ascertain authenticity. In either case a response may or may not be forthcoming to the client. If the server accepts the user, it returns a positive result with attributes containing configuration information. If the server rejects the user, it returns a negative result. If the server rejects the client or the shared "secrets" differ, the server returns no result. If the server requires additional verification from the user, it returns a challenge, and the request process begins again. RADIUS Configuration Examples This section contains examples of commands used to configure RADIUS settings on the switch. Device Security 113