Dell PowerVault TL2000 Manual - Page 5
September - iscsi interface
 |
View all Dell PowerVault TL2000 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 5 highlights
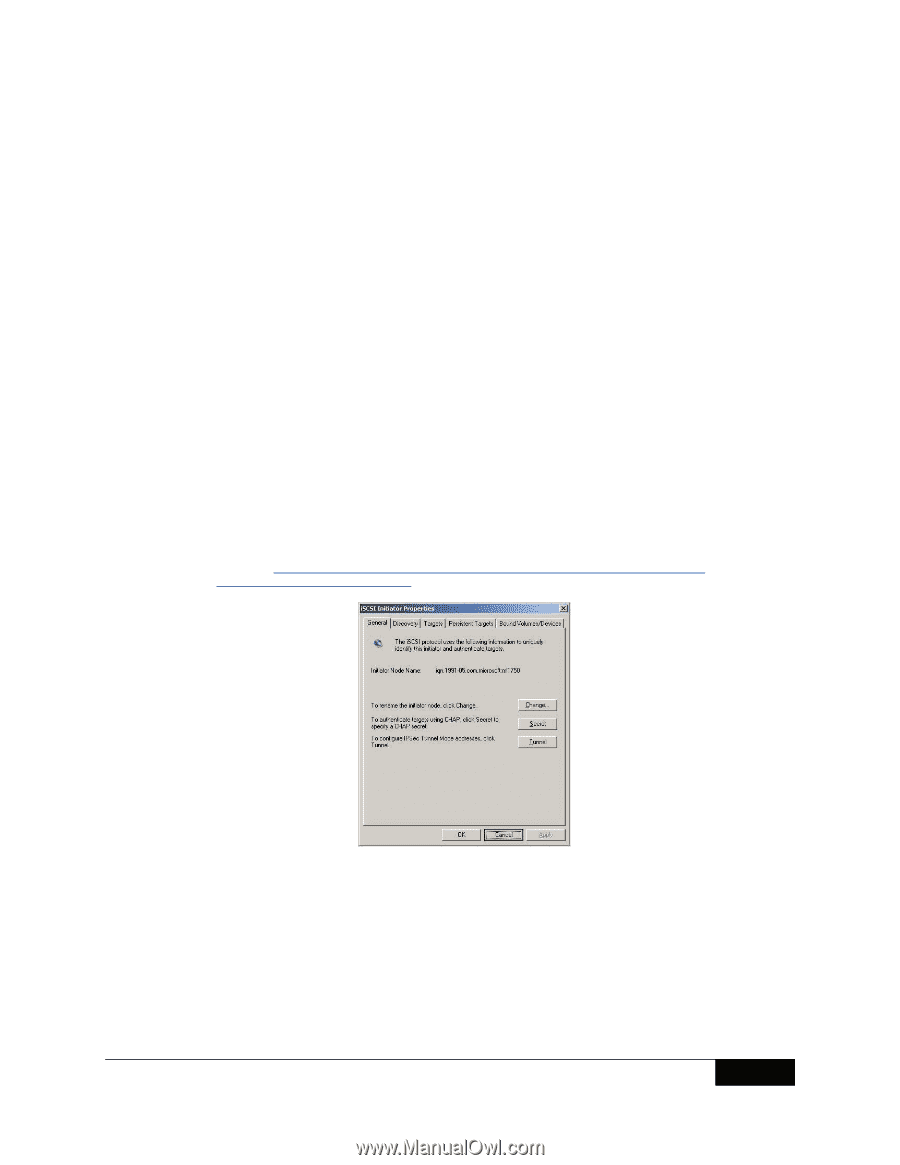
iSCSI for TL-Series Tape Libraries SECTION 3 iSCSI SAN SOLUTIONS To complement the Dell PowerVault MD3000i and Dell EqualLogic & EMC line of iSCSI interface disk storage systems, Dell has introduced an iSCSI-to-SAS Bridge Card for the Dell PowerVault TL2000 & TL4000 tape libraries. This card, when inserted into a TL-Series tape library, acts as an iSCSI target and provides SAS connectivity for LTO4, LTO4HH and LTO3HH tape drives. Best Practices: Oversubscription of the network switches can lead to many of the "performance" concerns often voiced about iSCSI networks. Using a dedicated, switched 1GbE switch such as the Dell PowerConnect 62XX or 54XX for iSCSI traffic is recommended. Should this prove unfeasible, deploying a PowerConnect 54XX iSCSI-optimized switch for combined traffic is recommended. It will detect iSCSI traffic and raise its Level of Service - in essence, providing more bandwidth to the iSCSI traffic. Best Practices: In most applications, exposing an iSCSI SAN to the internet can result in a security vulnerability and should be avoided if possible. While iSCSI does have some security features integrated into its specification (e.g., CHAP), it is typically a user-selectable feature and is not as robust as some other systems. Additionally, unless IPsec is implemented and enabled, data in-flight is transmitted "in the clear." Use of private, dedicated networks is strongly encouraged. SECTION 4 STEP-BY-STEP SETUP Servers connected to the iSCSI SAN will require an iSCSI initiator. Since most servers are Windows-based, Microsoft's iSCSI Initiator is a cost effective solution, available as a free download: http://www.microsoft.com/downloads/details.aspx?FamilyID=12cb3c1a-15d6-4585b385-befd1319f825&DisplayLang=en. Once installed, the set-up and use is straight-forward. Figure 1 : Microsoft's iSCSI Initiator The important consideration on this screen is the use of CHAP (Challenge Handshake Authentication Protocol). This is the main security apparatus in iSCSI. If your iSCSI SAN is visible to the external internet, it is highly recommended to enable this feature. Even with the availability of CHAP, it is still recommended to keep the iSCSI SAN private and not visible to the outside world. SEPTEMBER 2008 5