HP 635n HP Jetdirect Security Guidelines - Page 6
HP Jetdirect Administrative Guidelines, SET 1 - jetdirect ipsec ipv6
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 6 highlights
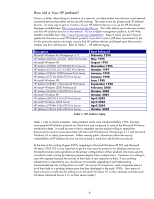
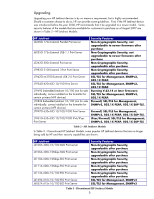
As you can see, replacing a discontinued 400n MIO model with a new external parallel port print server like the 300X will not upgrade the security capabilities of the Jetdirect device. Printers that have an MIO slot like the LaserJet IIIsi and LaserJet 4si have been discontinued for many years. Printers and MFPs with an EIO slot are still being sold today. The EIO slot was introduced on the HP LaserJet 4000 almost ten years ago. One of the great features of having an EIO based printer is the ability to install a J7961G 635n IPv6/IPsec print server. Using this product, we can take an older printer like the HP LaserJet 4000 and give it the latest in networking protocol and security support. This flexibility will come in handy as we evaluate the various attacks employed against HP Jetdirect and some ways to counteract those attacks. For companies with a lot of EIO based printers, proper deployment of the 635n can protect their printer/MFP investment and increase the security of their printing and imaging infrastructure. HP Jetdirect Administrative Guidelines In the material that follows, this whitepaper will be addressing some public information available about vulnerabilities or attacks against HP Jetdirect. In order to properly recommend configurations for HP Jetdirect, four different administrative guidelines will need to be used. These administrative guidelines come from the four main HP Jetdirect product lines, referred to as SETs. • SET 1: The 170x, 300x, 500x, 510x, 400n, 600n models. The administrative guideline for securing these devices is located here: http://h20000.www2.hp.com/bizsupport/TechSupport/Document.jsp?objectID=bpj05999. As a reminder, these devices do not have cryptographic security capability. • SET 2: The 610n, 615n, 620n, 625n, en3700, and Embedded Jetdirect (J7949E) models. SET 2 can use the administrative guideline referenced for SET 1 products, but a more updated administrative tool available via the EWS for securing these devices is located here: http://h20000.www2.hp.com/bizsupport/TechSupport/Document.jsp?objectID=bpj07576 • SET 3: The 630n and Embedded Jetdirect (J7982E, J7987E, J7991E, and J7992E) models. SET 3 can use the administrative guideline referenced for SET 2 products, but have additional security by means of a Firewall. The Firewall can allow/drop packets on the basis of IPv4/IPv6 addresses as well as service types. • SET 4: The 635n model and the CM8000 Color MFP series (J7974E). These models have the most security capability in HP Jetdirect's product line. With security configurations, one must be careful not to lock the front door and leave your windows open. In many cases, one must "lock down" several things before securing one thing can be effective. Before using the techniques presented here, the administrator at the very least should do the following: • Update all HP Jetdirect firmware to the highest level. One of the easiest ways to perform this operation is to use the HP Download Manager available at http://www.hp.com/go/dlm_sw. Using Internet Mode, the HP Download Manager will automatically indicate which devices need to be upgraded. HP recommends always upgrading only a few devices and performing an evaluation of those devices on your network before upgrading all devices to the latest firmware. • An Embedded Web Server (EWS) password has been specified • The default SNMPv1/v2c SET Community Name has been changed • All non-active protocols have been disabled (e.g., IPX/SPX, AppleTalk) • Mark any product that cannot be firmware upgraded to the highest level as a security risk. 6