HP 635n HP Jetdirect Security Guidelines - Page 7
HP Jetdirect Hacks: TCP Port 9100, V.33.14/V.33.15, K.08.49, L.25.57, H.08.60, V.28.22, V.36.11 - jetdirect ipv6 ipsec
 |
UPC - 882780301016
View all HP 635n manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 7 highlights
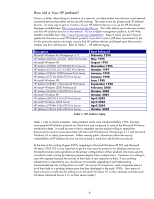
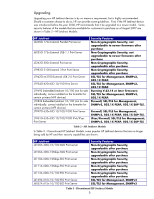
• A guideline to popular HP Jetdirect devices and the firmware they should be running as of August of 2007 is shown in Table 4: HP Jetdirect Product Number J7949E Embedded Jetdirect J4100A 400n 10Mbps MIO Print server J4106A 400n 10Mbps MIO Print server J3110A 600n 10Mbps EIO Print server J3111A 600n 10Mbps EIO Print server J3113A 600n 10/100 EIO Print server J4169A 610n 10/100 EIO Print Server J6057A 615n 10/100 EIO Print Server J3263A/J3263G 300x External Print server J3265A 500X External 3-Port Print Server J7983G 510X External 3-Port Print Server J7942A/J7942G en3700 External USB 2.0 Print Server J7934A/J7934G 620n EIO 10/100 Print Server J7960A/J7960G 625n EIO 10/100/1000 Print Server J7961A/J7961G 635n EIO 10/100/1000 IPv6/IPsec Print Server Firmware Version V.33.14/V.33.15 K.08.49 K.08.49 G.08.49 G.08.49 G.08.49 L.25.57 R.25.57 H.08.60 J.08.60 J.08.60 V.28.22 V.29.20 V.29.29 V.36.11 Table 4 - Jetdirect Firmware Versions NOTE: For some Embedded Jetdirect products, you'll need to upgrade the printer/MFP firmware to update the JDI firmware. Now that we covered enough background information, let's look at some of the reported vulnerabilities and attacks on HP Jetdirect. HP Jetdirect Hacks: TCP Port 9100 TCP port 9100 was one of the first ways developed for sending print data to a printer. Some public references talk about a print protocol that exists on TCP port 9100. There isn't one. Raw data delivered to the TCP layer on the HP Jetdirect device is sent to the printer as if it had been delivered over a parallel port, serial port, or any other port. TCP port 9100 is the fastest and most efficient way of delivering data to a printer using the TCP/IP protocol suite. The most common hack for TCP Port 9100 is send a job to that port that has some PJL commands in it. These PJL command can do a variety of things, one of the most common ones being to change the control panel display. Remember that HP Jetdirect is stripping off the TCP/IP headers and presenting this data directly to the printer. The printer is processing the PJL (data) as if the printer was directly connected to a PC. Many years ago, printer drivers would use the PJL command suite to control the printer in a variety of ways. As we can see, in the networking world, there is a potential for misuse. How does an Administrator prevent TCP Port 9100 from being misused? Based upon what we've learned about HP Jetdirect so far, we know we have to control who can and who cannot establish a TCP connection to TCP Port 9100. Table 5 shows us some options, presented in the form of the least amount of security (option 1) to higher levels of security (options > 1): 7