HP Nc6220 HP ProtectTools: Authentication technologies and suitability to task - Page 6
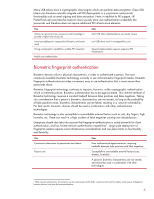
Biometric fingerprint authentication
 |
View all HP Nc6220 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 6 highlights
Many USB tokens have a cryptographic chip/engine which can perform data encryption. These USB tokens can therefore naturally integrate with PKI deployments in a corporation and provide functionality such as email signing and data encryption. Note: In addition to PKI support, HP ProtectTools also provides the means to more securely store user authentication credentials like passwords and therefore does not require additional PKI infrastructure elements. Pros Utilizes two personal traits, possession and knowledge to provide a higher level of security Lower cost deployment compared to Biometrics and smart cards Strong cryptographic capabilities, enables PKI integration. Mobile user authentication Cons Most USB token implementations are vendor unique Lost USB tokens result in manageability costs General implementation requires expensive PKI infrastructure. Biometric fingerprint authentication Biometric devices utilize a physical characteristic in order to authenticate a person. The most commonly available biometric technology currently in use is the biometric fingerprint reader. Biometric fingerprint authentication provides convenient, easy to use authentication that is more secure than passwords alone. Biometric fingerprint technology continues to improve; however, unlike cryptographic authentication which is extremely precise, Biometric authentication has to be approximated. This inherent attribute of Biometric technology requires a constant tradeoff between false positives and false negatives. Taking into consideration that a person's biometric characteristics are not secrets, as long as the probability of false positives exists, biometric characteristics can be faked, resulting in a security vulnerability. For best results, biometric devices should be used in combination with other authentication technologies. Biometric technology is also susceptible to unavoidable external factors such as cuts, dry fingers, high humidity, etc. These can result in a high incident of false negatives causing user dissatisfaction. Enterprises should also take into account that fingerprint authentication is suited primarily for client authentication, and has limited network authentication capabilities3. Large scale deployment of fingerprint readers requires some infrastructure considerations and can place limits on functionality and flexibility. Pros Convenient alternative to passwords and tokens Easy to use Cons Uses mathematical approximations, requiring tradeoffs between false positives and false negatives Susceptible to unavoidable external factors (cuts, dryness, humidity) A person's biometric characteristics are not secrets, and should be used in combination with other technologies. 3 While network authentication for biometrics can be implemented, the flexibility would be limited and the solution would require all deployed biometric devices to be from the same manufacturer. 6