HP Nc6220 HP ProtectTools: Authentication technologies and suitability to task - Page 7
Virtual token authentication, Feature Comparison and suitability to task
 |
View all HP Nc6220 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 7 highlights
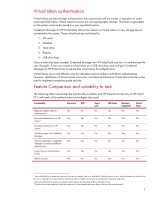
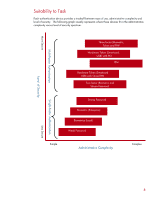
Virtual token authentication Virtual tokens provide stronger authentication than passwords and are similar in operation to smart cards and USB tokens. Virtual tokens however are not cryptographic devices. The token is generated on the system and can be stored in a user specified location. Credential Manager for HP ProtectTools allows the creation of Virtual tokens on any storage device connected to the system. These include but are not limited to: 1. SD cards 2. Diskettes 3. Hard drive 4. Registry 5. USB drive keys Once a token has been created, Credential Manager for HP ProtectTools can use it to authenticate the user. Example: A user can create a virtual token on a USB drive key, and configure Credential Manager for HP ProtectTools to require that virtual token for authentication. Virtual tokens are a cost effective way for individual users to achieve multi-factor authentication. However, distribution of Virtual tokens cannot be controlled and therefore Virtual tokens should not be used to implement enterprise grade security. Feature Comparison and suitability to task The following table summarizes the functionality available with HP ProtectTools Security on HP Client PC's with each of the authentication technologies discussed. Functionality Password TPM Requires multiple traits for No No authentication4 Pre-boot Authentication on HP Yes Yes clients 5 Drivelock protection on HP Yes Yes clients 6 Windows Logon via Credential Yes Yes Manager Can be combined in credential Yes Yes manager to provide multifactor authentication Single Sign-on authentication Yes Yes access Identity backup No No Smart card Yes Yes No Yes Yes USB token Yes Biometric fingerprint No Virtual token Yes No No No No No No Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes Yes No Yes 4 User authentication is based on three traits that can be uniquely tied to an individual. What the person knows, what the person has and who the person is. Utilizing two or more traits to authenticate offers a higher level of security compared to utilizing a single trait. 5 Pre-boot authentication requires user authentication before the operating system is allowed to load. 6 Drivelock technology requires a hard drive password to be entered before any data on the hard drive can be read. 7