HP t5710 HP Sygate Security Agent User Guide - Page 39
Description, Name of, Parameter, Monitoring and Logging
 |
View all HP t5710 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 39 highlights
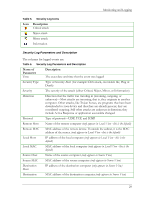
Monitoring and Logging Table 5. Security Log Icons Icon Description Critical attack Major attack Minor attack Information Security Log Parameters and Description The columns for logged events are: Table 6. Security Log Parameters and Description Name of Parameter Time Description The exact date and time that the event was logged Security Type Type of Security Alert (for example: DoS attack, executable file, Ping of Death) Severity The severity of the attack (either Critical, Major, Minor, or Information) Direction Direction that the traffic was traveling in (incoming, outgoing, or unknown)-Most attacks are incoming, that is, they originate in another computer. Other attacks, like Trojan horses, are programs that have been downloaded to your device and therefore are already present; they are considered outgoing. Still other attacks are unknown in direction; they include Active Response or application executable changed. Protocol Type of protocol-UDP, TCP, and ICMP Remote Host Name of the remote computer (only appears in Local View - this is the default) Remote MAC MAC address of the remote device. If outside the subnet, it is the MAC address of the router. (only appears in Local View - this is the default) Local Host IP address of the local computer (only appears in Local View - this is the default) Local MAC MAC address of the local computer (only appears in Local View - this is the default) Source Host Name of the source computer (only appears in Source View) Source MAC MAC address of the source computer (only appears in Source View) Destination Host IP address of the destination computer (only appears in Source View) Destination MAC address of the destination computer (only appears in Source View) 29