Ricoh Aficio MP C3001 Security Target - Page 43
Security Objectives Rationale - review
 |
View all Ricoh Aficio MP C3001 manuals
Add to My Manuals
Save this manual to your list of manuals |
Page 43 highlights
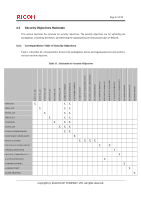
Page 42 of 93 4.3 Security Objectives Rationale This section describes the rationale for security objectives. The security objectives are for upholding the assumptions, countering the threats, and enforcing the organisational security policies that are defined. 4.3.1 Correspondence Table of Security Objectives Table 11 describes the correspondence between the assumptions, threats and organisational security policies, and each security objective. Table 11 : Rationale for Security Objectives O.DOC.NO_DIS O.DOC.NO_ALT O.FUNC.NO_ALT O.PROT.NO_ALT O.CONF.NO_DIS O.CONF.NO_ALT O.USER.AUTHORIZED OE.USER.AUTHORIZED O.SOFTWARE.VERIFIED O.AUDIT.LOGGED OE.AUDIT_STORAGE.PROTCTED OE.AUDIT_ACCESS_AUTHORIZED OE.AUDIT.REVIEWED O.INTERFACE.MANAGED OE.PHYSICAL.MANAGED OE.INTERFACE.MANAGED O.STORAGE.ENCRYPTED O.RCGATE.COMM.PROTECT OE.ADMIN.TRAINED OE.ADMIN.TRUSTED OE.USER.TRAINED T.DOC.DIS X X X T.DOC.ALT X X X T.FUNC.ALT X X X T.PROT.ALT X X X T.CONF.DIS X X X T.CONF.ALT X X X P.USER.AUTHORIZATION X X P.SOFTWARE.VERIFICATION X P.AUDIT.LOGGING X XXX P.INTERFACE.MANAGEMENT X X P.STORAGE.ENCRYPTION X P.RCGATE.COMM.PROTECT X A.ACCESS.MANAGED X A.ADMIN.TRAINING X A.ADMIN.TRUST X A.USER.TRAINING X Copyright (c) 2011 RICOH COMPANY, LTD. All rights reserved.